10,000 years to a few seconds
In 2019, Google’s quantum computing team showed that Sycamore, their 53-qubit quantum processor—originally a 54-qubit processor, but one qubit bit the dust—was able to process a problem in 200 seconds that would take the most powerful supercomputer over 10,000 years. It was a moment dubbed “quantum supremacy” where classical computers were trounced by the shiny new kid on the block – even if it was a problem with no practical applicability.
Even though Sycamore only demonstrated the vast power of quantum computing in an academic sense, the mere existence of quantum supremacy is a key moment in the development of this new technology. Just as we hold 100,000 times more computing power in our hands than the onboard computer that guided Apollo 11 to the moon, the possibilities – good and bad – of quantum computing are now coming into view.
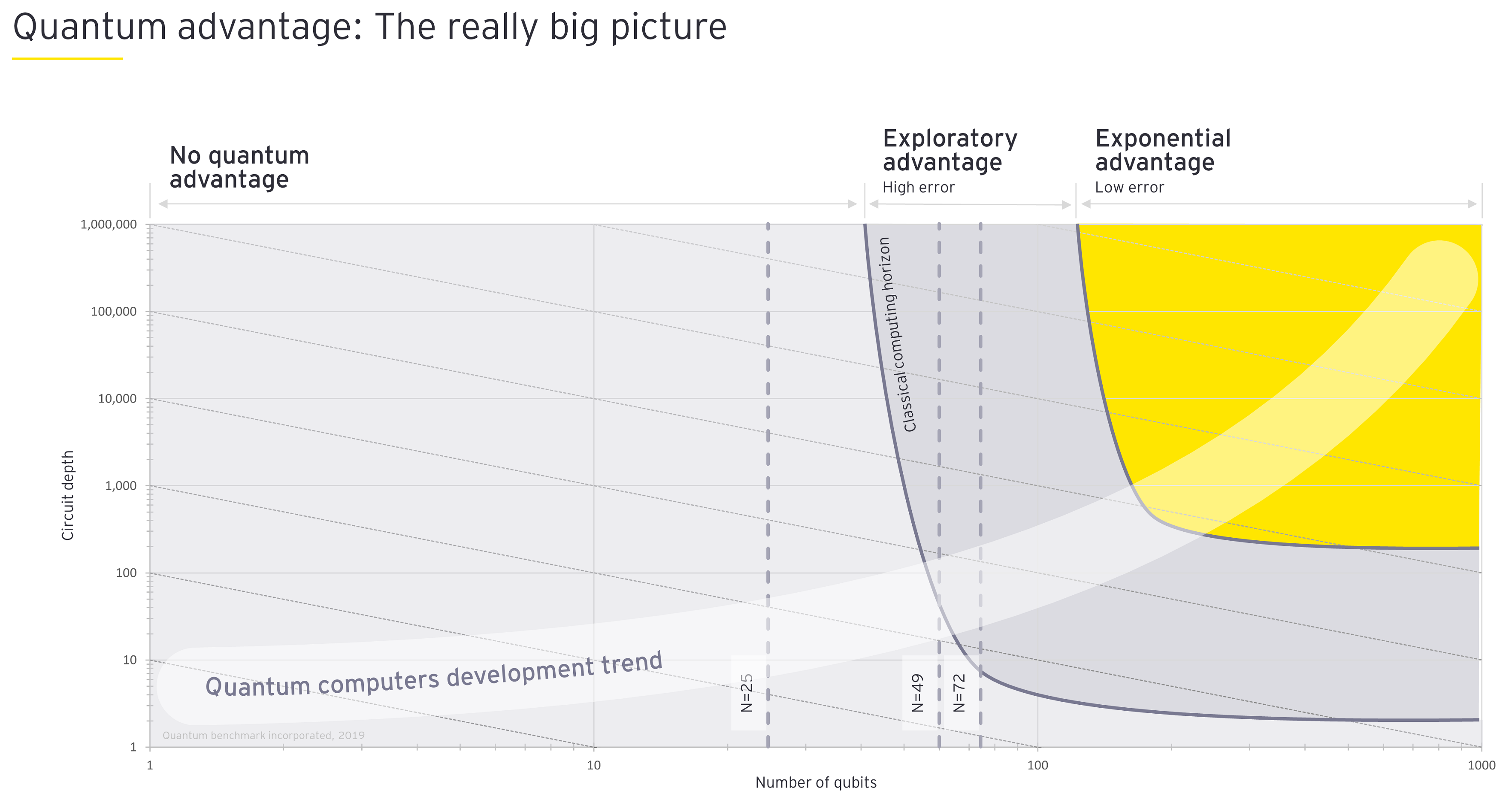
Figure 2: As quantum computers add more qubits to their processing power (x-axis), the quantum advantage comes when the stability of those qubits (or the circuit depth, shown on the y-axis) also increases. Real revolutionary change arrives when both the number of qubits and the stability of those qubits reach the yellow zone.
Similar to the early missions of the Apollo project, in four decades quantum computing hasn’t quite managed to mature into the besuited, middle-aged expectations Benioff might have had. Instead, it’s more of an unruly teenager. Or, as one expert says, multiple unruly teenagers.
Sven Rogge has been working on the hardware side of quantum computing for almost two decades, starting in Germany, moving to the US, the Netherlands and now as a professor at the Centre for Quantum Computation and Communication Technology at the University of New South Wales. In the quantum computing world, there are a few spearheading technologies with very different approaches,” he says.
You can think of all the different types of technology basically as a class of misbehaving teens. Some things that seem to work out pretty neatly, may not go anywhere. But it may be the one crazy teenager who never behaved, that actually pulls themselves together and comes out as the long-term solution.
EY Australia Cyber Security Senior Manager Alexey Bocharnikov says that a lot of effort is going into improving the stability of qubits. “They are pretty noisy today and live for less than a second,” he says. “We’re in the NISQ era – the Noisy Intermediate-Scale Quantum era. Noisy, because we have noisy qubits, and intermediate-scale, because we have relatively small quantum computers.”
According to Rogge, today no one can honestly say they know which of the different types of quantum computing will persist. Much of the research is still working on parallel tracks. Complicating the picture is the fact that the software is also in development as is the nascent field that sorts problems into those that are optimal for standalone quantum computers, classical computers or a hybrid solution.
According to the MIT Technology Review, the software that runs on quantum code won’t be readily transferable between the different types of quantum computing. Perhaps they may not even be transferable between different iterations of the same quantum computer. “Quantum code … has to be highly tailored to the qubits it will run on, so as to wring the most out of their temperamental performance,” writes MIT’s Gideon Lichfield. “That means the code for IBM’s chips won’t run on those of other companies, and even techniques for optimizing Google’s 53-qubit Sycamore won’t necessarily do well on its future 100-qubit sibling. More important, it means nobody can predict just how hard a problem those 100 qubits will be capable of tackling.”
While IBM and Google have set ambitious targets for the next ten years, and the CSIRO has earmarked quantum technology as having the potential to generate over $4 billion and 16,000 jobs for the Australian economy by 2040, there’s another factor that will be critical to the success of the field: finding students with the capacity to work on quantum technology.
“One of the huge challenges for people who are new to the field,” says Michael Bremner, Professor of Computer Science at the Centre for Quantum Software and Information and core member of the Sydney Quantum Academy, “is working out where to step in and what are the right sorts of problems to assess. Education and training is critical right now because quantum technology has got everyone’s attention but the human capacity hasn’t caught up.”
Four things to improve your quantum defences
Want to improve your quantum resilience? Here are four current but evolving methods that organisations should be considering.
- Bolster your cryptography agility. Simply put, it is replacing an existing cryptographic algorithm with a new, quantum resilient algorithm. But it’s far from a simple problem. Engineers and program managers need to audit their code and applications to find and substitute a stronger cryptographic solution.*
- Make breaking code uneconomic. The cost of an attack should not outweigh the potential gain. Encrypting small pieces of data with a unique cryptography key will make an attack economically unfeasible. One bit of data is not valuable for an attacker, as decrypting all the pieces of data becomes too expensive.
- Use longer keys for symmetric cryptography algorithms. Quantum computers pose a different level of risk to different cryptography algorithms. Symmetric cryptography algorithms remain relatively secure if a long-enough key is used. Organisations should avoid using short keys (64 bit and 128 bit) and replace them with longer variants (256 bit).*
- Quantum Key Distribution. Classical key exchange solutions (Public Key algorithms) become particularly vulnerable in a post-quantum world. Quantum Key Distribution (QKD) is a technology replacing this link in a chain. The crux of the technology is the continuous generation of a key between two nodes using quantum hardware. The key is known only to those two nodes. The security of key exchange is provided by the performance of light particles and ensured by limitations imposed by quantum physics, meaning that QKD remains a secure way of key exchange in a post-quantum world.*
*www.quintessencelabs.com/quantum-safe-cyber-security
Unwelcome disruption or transformational opportunity
Just as we’re slowly getting a handle on what kind of quantum computing works and what doesn’t, we're also beginning to get a sense of the advantages and disadvantages of different technologies. “It's becoming very clear that a range of these quantum information technologies that we'll be developing will be useful in different contexts,” says Bremner, who also leads the Architecture and algorithms" theme in the ARC Centre for Quantum Computation and Communication Technology, “But the specifics of the problem matter and for those of us analysing problems that quantum computers can help with, we’re trying to develop mathematical tools that will make that job easier.”
The list of everyday applications that could be insecure in a quantum world today ranges from internet banking systems reliant on asymmetric cryptography and encrypted messaging applications to IoT (internet of things) devices and remote working VPNs. Of course, there are also many opportunities that quantum computing opens up. This includes brute-force traffic or medical trial optimisation problems, testing of large-scale systems from new-age aircraft, and smart energy grids to materials improvements and pharmaceutical development.
What we do know is that when quantum computing arrives, the effects will be profound. Some experts have described quantum computing as transitioning from scientific curiosity to technical reality. Think about a bank or government agency losing an encrypted file containing personal information—quantum decoding tools would make it very easy for someone to access that information. The upshot? Data that needs to remain secure over the long-term, needs to become quantum resilient now.
“It’s really important to understand that you can store attacks,” says Michael Bremner. “If you're using public cryptography systems to secure and send information that could be sensitive on a 20-year timeframe, you should probably be thinking about stopping doing that stuff today.”
The ability to store attacks has introduced key questions for many organisations and their IT security teams: are we going to have to change the way we do our internet security? And do we have teams that are capable of making these assessments? How will the systems impact user experience? What is the complexity of change? How will program-level changes effect system-wide security?
Over the past decade, many large companies, especially financial institutions, have answered these questions around cyber security infrastructure on a trade-off basis. At one end of the spectrum, pursuing infinite security at infinite cost is not an option. Similarly, merely pursuing reasonable security at reasonable cost comes with the potential for breaches to significantly impact an organisation’s ability to do business. Rather than optimising the systems for one or a handful of security variables, IT teams have tried to strike a balance.
To deal with critical, present-day threats rather than looming threats, such a quantum computers, savvy IT teams are beginning to preload their teams with as much context as possible.
“Quantum computing isn’t a problem until it’s a problem,” says the IT Manager for a large Australian bank, “as opposed to something like ransomware, which tends to grow linearly. And so, we've got a small collection of those kinds of potential step-change risks that we keep an eye on. And quantum computing is one of those.”
Related article

Figure 3: When will quantum technology impact your business?
Those on the cyber security front line understand that current-day cryptography has a limited life. When the unruly quantum teenager matures into a more menacing adult, those organisations that have built-in quantum agility will be better placed to deal with the implications.
It boils down to organisations having a clear understanding of where their high-value, high-exposure cryptography lies. They then need to implement flexibility around programmatically rotating those cryptography keys and potentially changing algorithms. They also need to keep a watching brief on both the rate at which quantum computing is improving and the potential answers that are emerging, whether those are traditional answers around key management or more sophisticated answers such as deploying post-quantum algorithms.
Why we need to be thinking quantum now
The US National Institute for Standards and Technology (NIST), run by the US Department of Commerce, is currently developing post-quantum algorithms that aim to be quantum resilient. This is far from an easy task. Algorithm developers not only need to grapple with unstable, emerging technology, but they need to assess whether the algorithm will be secure under both classical and quantum attack vectors. Furthermore, changing a system could open up other avenues of attack.
Most experts believe that NIST will announce their standards and recommendations for the new protocols in 2023. Those guidelines will give organisations a clear understanding of how secure their encryption systems are as well as which systems will get broken and their recommended alternatives. They can then choose to migrate to the new technology or potentially encapsulate the existing algorithms.
However, developments in technology make those timelines nebulous at best and risky at worst. Should quantum computing developments outstrip the cryptographic key technology, data suddenly becomes compromised. David Garvin is Principal Researcher Quantum Computing at NEC and was previously with Rigetti Computing. He has two decades of experience working in quantum technology and financial services including with large Australian banks. He says that not only do companies need to be aware of sudden advances in quantum computing capabilities, companies also need to factor in an implementation time.
If, in three years’ time, the cyber security department of a large organisation tells senior management out of the blue that their data isn’t safe due to quantum encryption breaking their systems and they need a large amount of money to fix it, it’s going to be a much harder sell than if you've been regularly briefing the leadership team over these next three years.
Legacy, as opposed to new systems, are especially vulnerable. To create quantum resilience, organisations need to look at compensating controls that wrap around them should the existing encryption become much less valuable. Before the post-quantum algorithms from NIST stabilise, companies are starting to insist on commercially available systems that can be readily retooled for quantum resilience. “We can’t adopt things that aren’t ready yet,” says the bank’s IT manager, “but we can make sure that we’re ready to adopt them as soon as the solutions are available.”
Still, getting organisations to move quickly, or even just gently warming them up for something that is a horizon risk, will always run into the question: why not wait to see if the threat eventuates, and then throw money at the problem? For Garvin, this approach carries large risks as well as missing the other side of the threat – the opportunity. “If you deal with the issue of quantum computing when it matures, not only are you searching for a solution at precisely the same time as everyone else, which will impede your ability to deal with the threat as efficiently as possible,” he says, “but you’re also missing out on developing all the institutional knowledge that comes with investigating it today.”
By starting the process now, he says, organisations give themselves time to methodically work through quantum technology and applications, allowing the knowledge and potential opportunities to pervade the business. “Even in the classical computing environment, all this takes time,” says Garvin, “but if you set up a team now, it gives them a chance to get their heads around all the security implications, the data implications and the network implications in a managed and planned manner.”
Summary
Exponential computing power – quantum computing – has the potential to improve our world immensely. Data held under current security regimes will be vulnerable to attack through ‘storing’ – and it may only be years away. Rather than wait, cyber leaders must forewarn their organisations as advances will come suddenly.



