In some areas, the convergence makes the environment more complex to protect, providing attackers with millions of potential entry points. The rollout of smart meters and connected home initiatives are prime examples.
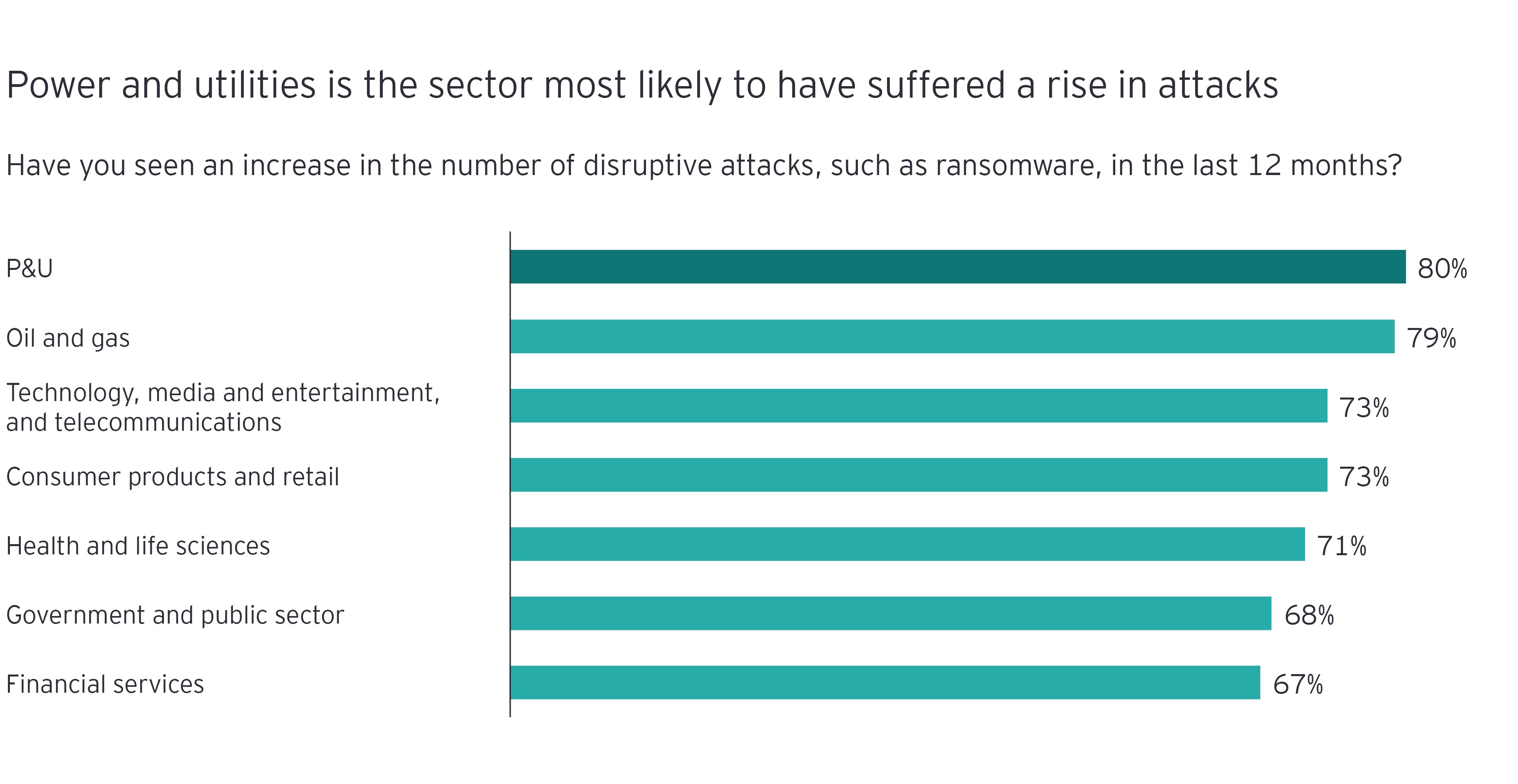
Moreover, sophisticated and well-resourced crime groups understand the potential for ransomware in an industry where operational shutdowns can quickly become a national emergency. State-sponsored groups also see cyber attacks on their rivals’ critical infrastructure as a powerful weapon. Indeed, 40% of P&U leaders believe that state-affiliated actors are behind the breaches they have suffered, compared with only 24% of CISOs in other sectors who say the same.
How P&U leaders can respond
To succeed within a challenging internal and external environment, P&U CISOs need to take action, embed security by design, and consider risk and security from the outset.
Make a broader case for funding
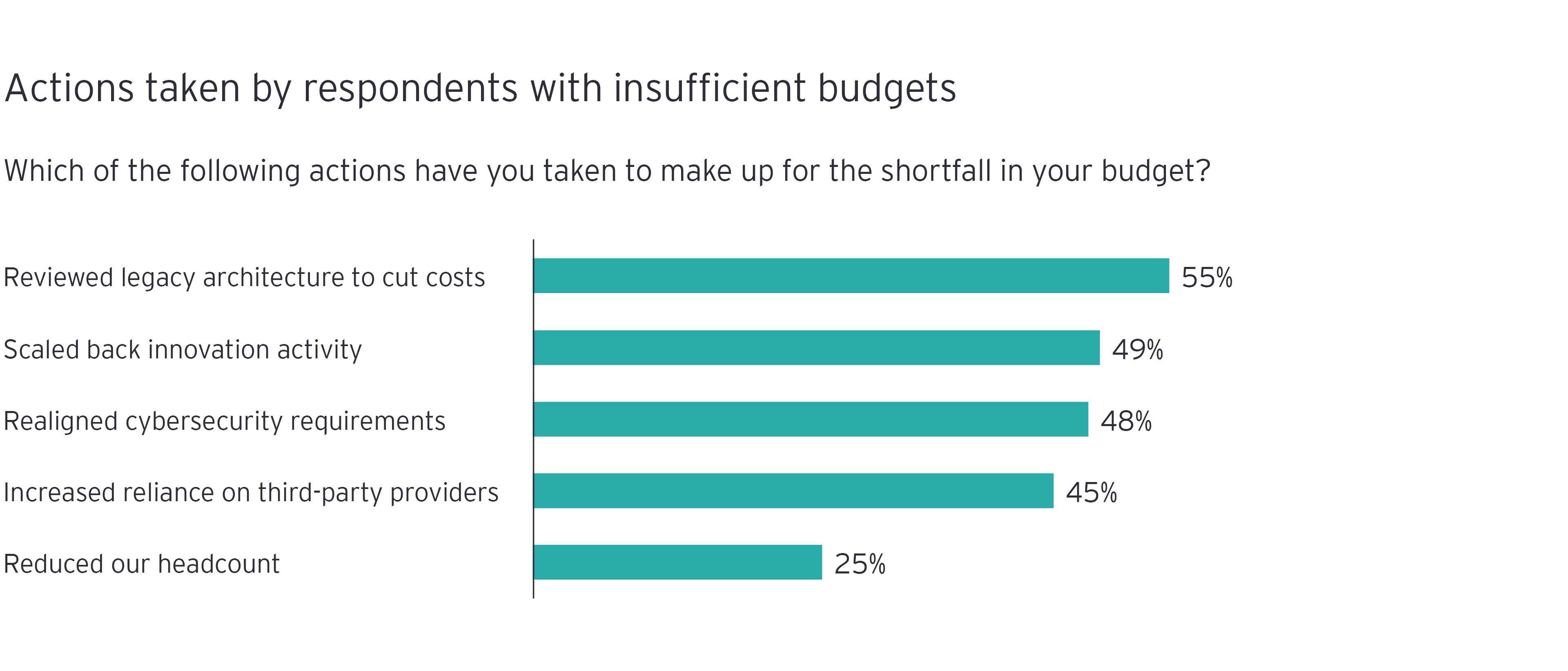
Threat actors have started targeting the P&U sector with ever-greater frequency, exploiting justifiable concern about any interruption to the population’s power or water supply. The research suggests, however, that cybersecurity funding has not kept up with the growing risk.
Currently, P&U cybersecurity leaders say that citing risk reduction and emerging threats is their preferred way to justify new funds (42%). As attacks increase, they should highlight the importance of response and recovery as well as prevention, to build a more broad-based argument for resources. “You need to accept there are going to be attacks and that some will be successful, so the business case is for a budget that goes beyond just prevention,” explains Firth.
Update the language and reference points of cybersecurity
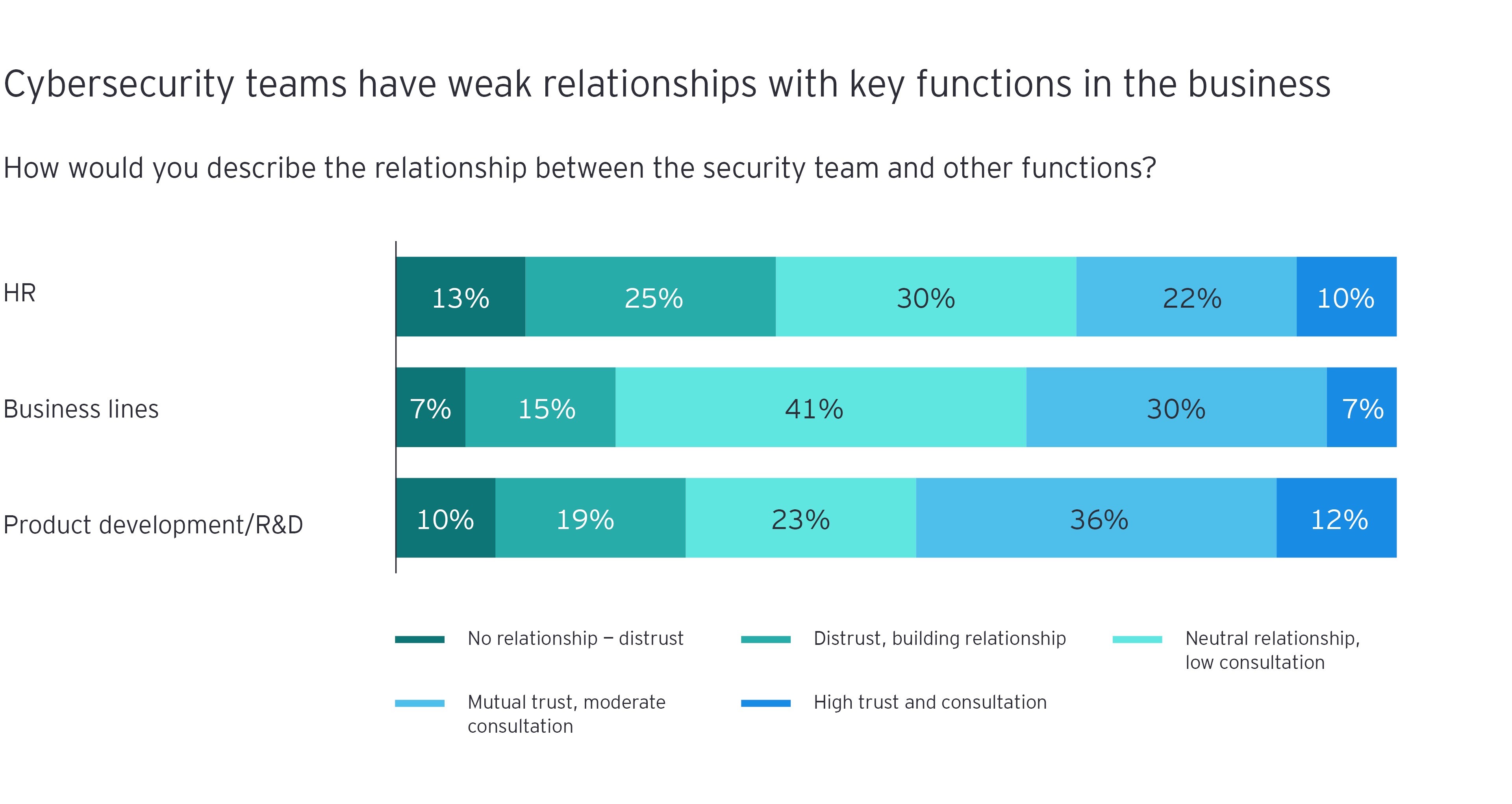
Cybersecurity functions are struggling to build close relationships across the business – often among engineering teams that oversee the most critical systems and operational data. Overcoming these differences is not just a case of learning to use specific terminology and frames of reference, but also recognizing that discrete cultures exist in different pockets of the business.
Firth suggests that CISOs should adopt multiple perspectives to build bridges. “The problem is that many CISOs came up through IT, and today, there is a paradigm clash between IT and OT,” he explains. “On one hand, you’ve got engineers focused on availability and safety, on systems that are potentially decades old. On the other, you’ve got a CISO urging them to patch the system straight away because of confidentiality and integrity concerns. It’s a real stress point.”

 A local perspective
A local perspective