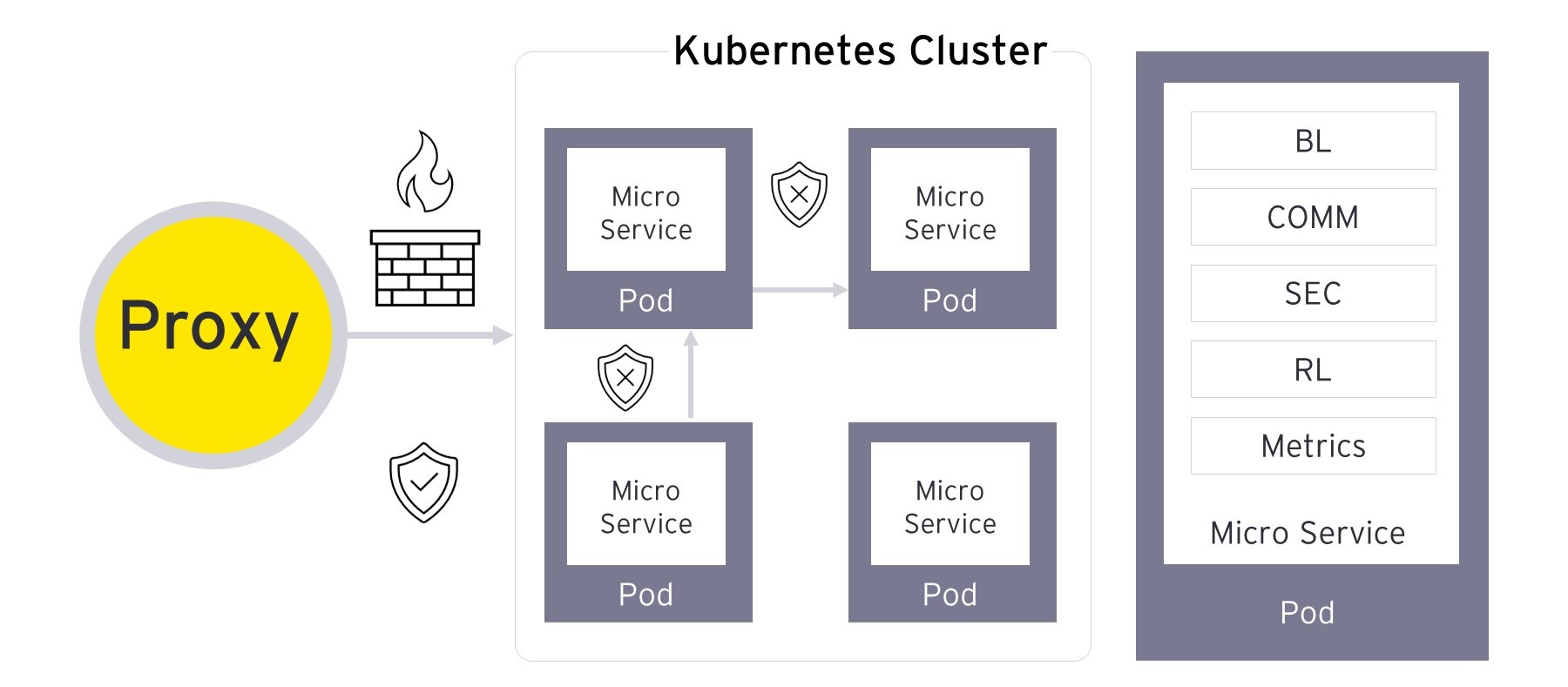
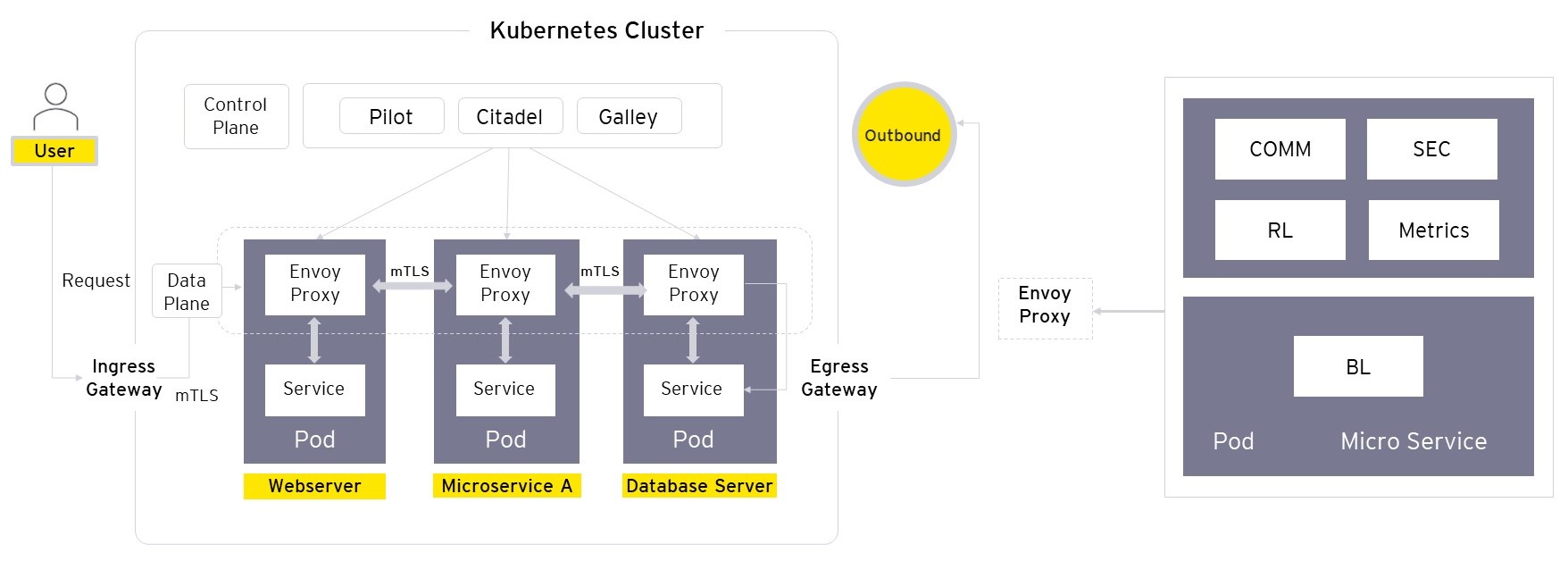
Without an enterprise service mesh platform, contemporary applications with a microservices-based architecture would have a much larger overhead in terms of design, development, and maintenance. Right from maintaining separate business logic and configuration specs to complex authentication and authorization implementations that are custom to the application, developers will have to spend a lot of time gluing together disparate technology components.
With an application developed through a service mesh implementation, developers can let the platform do much of the heavy lifting in terms of inter/intra communication, traffic routing between microservices, load balancing, policy enforcement, workflow and configuration safeguards. This allows development teams to focus primarily on using the right design patterns, efficient business logic, and other aspects.
A service mesh improves the microservices architecture as it enables companies or individuals to create robust enterprise applications, made up of many such microservices on a hosting platform of their choice.
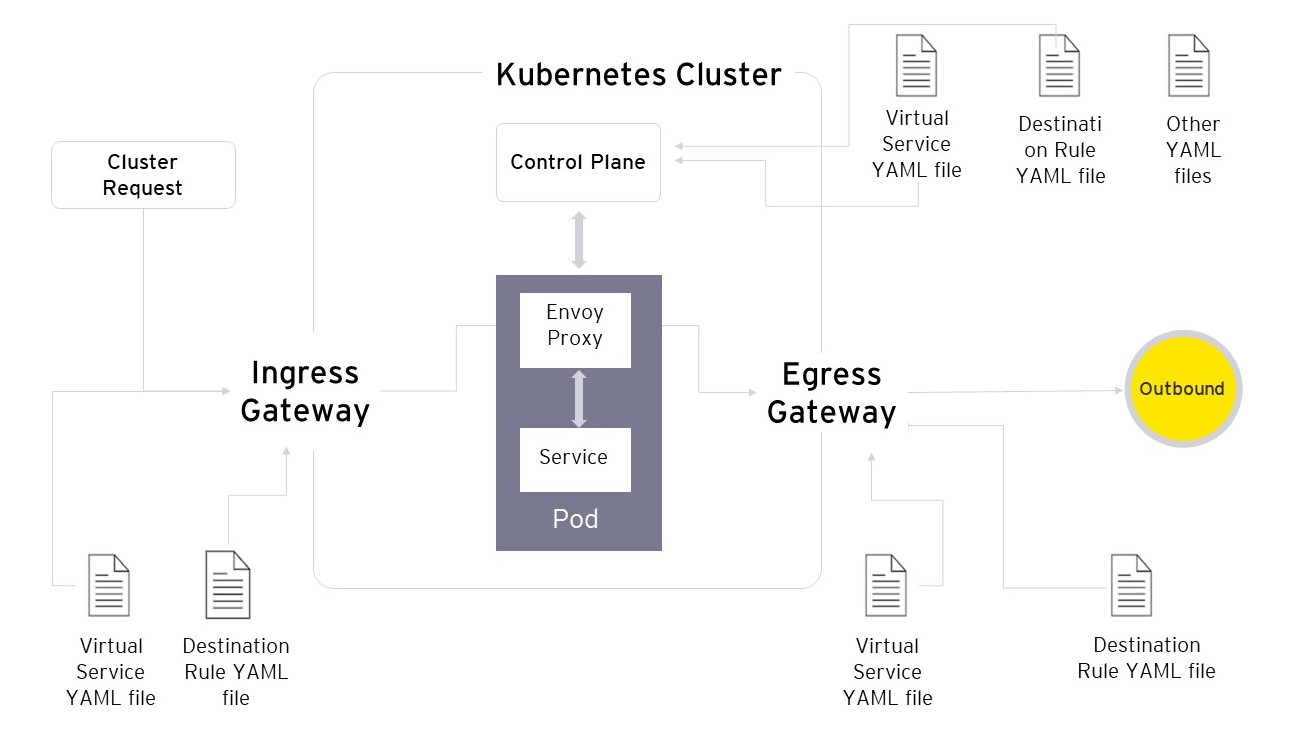
An enterprise service mesh solution allows developers to focus on adding business value to each service they build, rather than worrying about how each service communicates with the rest. For DevOps teams that have an established production continuous integration and continuous deployment (CI/CD) pipeline, a service mesh can be essential for programmatically deploying apps and application infrastructure to manage source code and test automation tools seamlessly.
Related content
Summary
Organizations use multiple cloud service providers to improve performance through speed and agility, but also must contend with different technology stacks, higher costs, security risks, and limited visibility of communication between the loose combinations of cloud-based microservices and applications. Adopting an enterprise service mesh allows organizations to manage and monitor microservices, including security features. This system can manage traffic and rules, allowing developers to focus on other beneficial tasks.


