EY BlackShark
The objective for all organizations should be not only to protect the enterprise with good cybersecurity hygiene and basic lines of defense, but also to optimize the response with more advanced tools and strategies. As digital transformation develops, cybersecurity must be an enabling function rather than a block to innovation and change.

EY BlackShark
Protect the enterprise
Cyber risks are evolving and any organization that regards itself as safe from cyber attacks is likely to be in for a shock.
The objective for all organizations should be not only to protect the enterprise with good cybersecurity hygiene and basic lines of defense, but also to optimize the response with more advanced tools and strategies. As digital transformation develops, cybersecurity must be an enabling function rather than a block to innovation and change.
The number of fake emails sent worldwide every day.
6.4 bilionDark Reading, August 27, 2018. [https://www.darkreading.com/endpoint/64-billion-fake-emails-sent-each-day/d/d-id/1332677]
The challenge for organizations is to progress on three fronts:

EY Blackshark
Cyber Analytics and intelligence platform
Cyber risks are evolving and any organization that regards itself as safe from cyber attacks is likely to be in for a shock.
Our solution
EY BlackShark is a SaaS solution that is enabling organizations to gain insights from their external IT attack surface and uncover possible weak point that can be exploited by cyber threats.
Our solution is most useful for medium to large organizations who have a significative internet presence or critical services operators (as defined under the NIS Directive) who need to manage their cyber exposure.
EY BlackShark operates at the first phases of the Intrusion Kill Chain model:
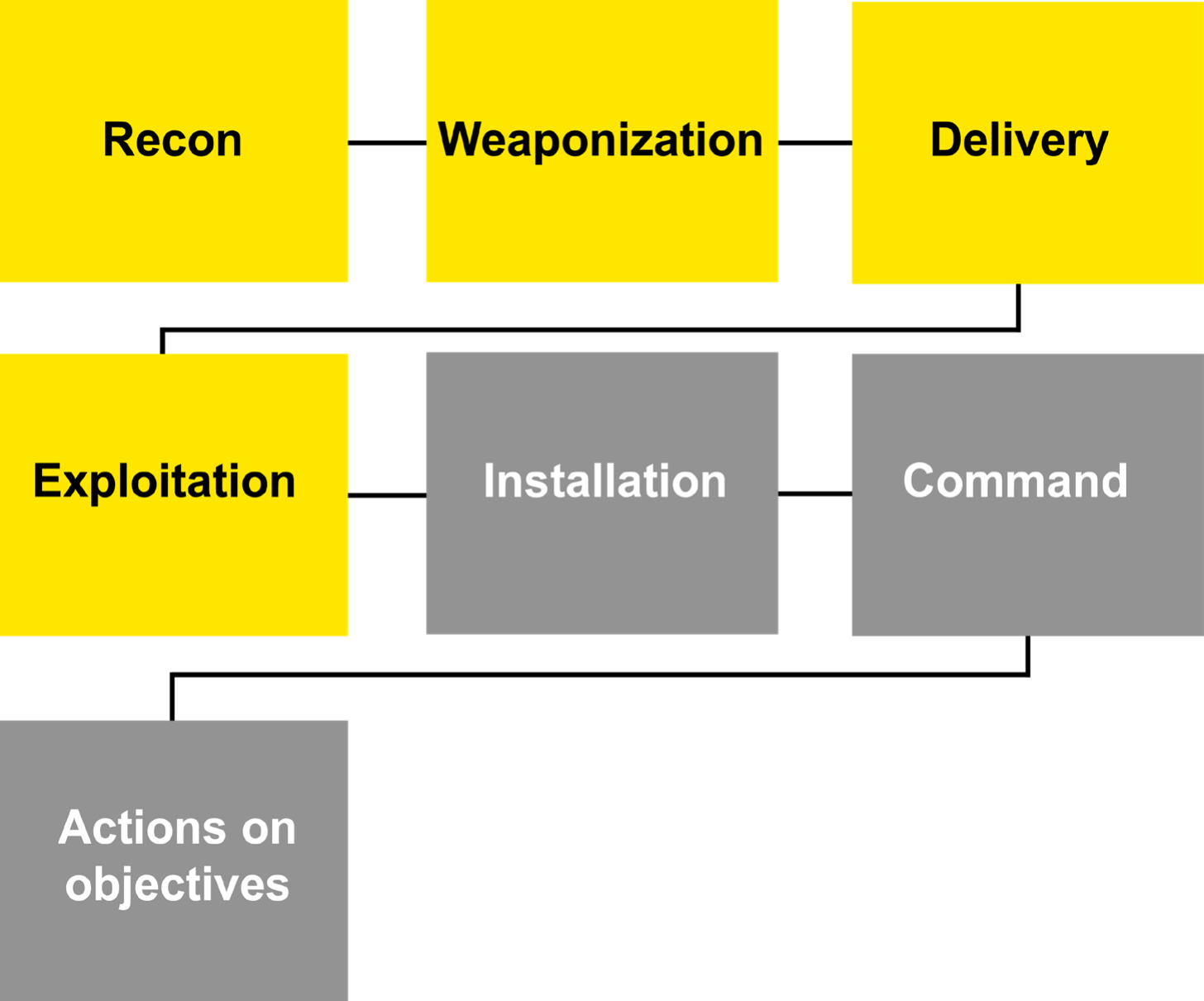
Our solution helps you identify:
An interactive dashboard displaying all managed and unmanaged IT assets of an organization including the following:
- IP Addresses
- DNS names
- Hosting and ISP
- Location and Geography
- Exposed IoT and ICS components
- Unmanaged IT assets and phishing infrastructure
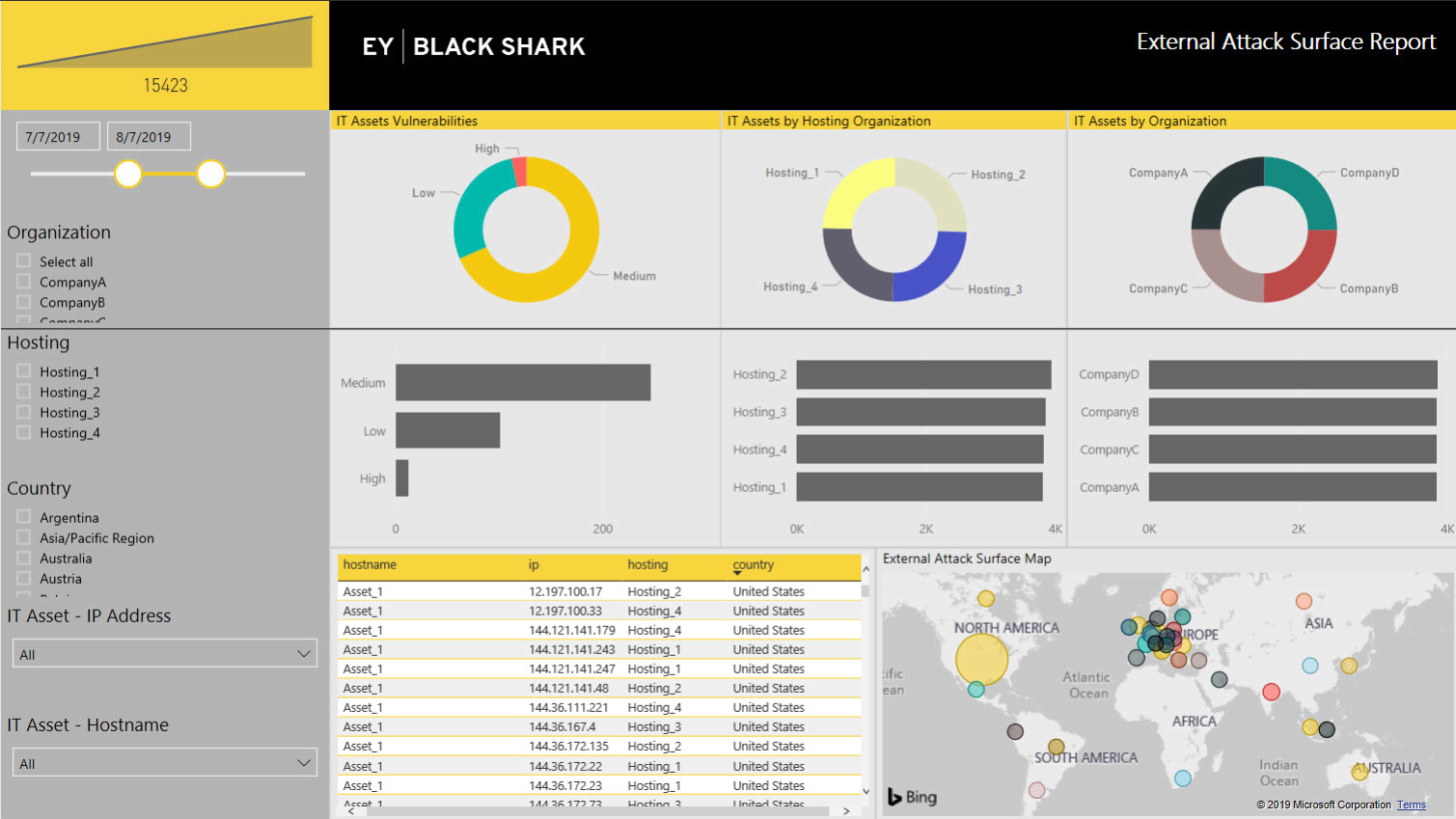
- IT Assets Vulnerabilities
- IT Assets by Hosting
- Organization
- IT Assets by Organization
- External Attack Surface
An interactive dashboard displaying validated and unvalidated identified vulnerabilities for all identified IT assets including:
- CVE / CWE identification
- Vulnerability description
- Risk
- Affected component
- Affected IT asset
- Mitigation recommendations
- Vulnerability validation (exploitation)
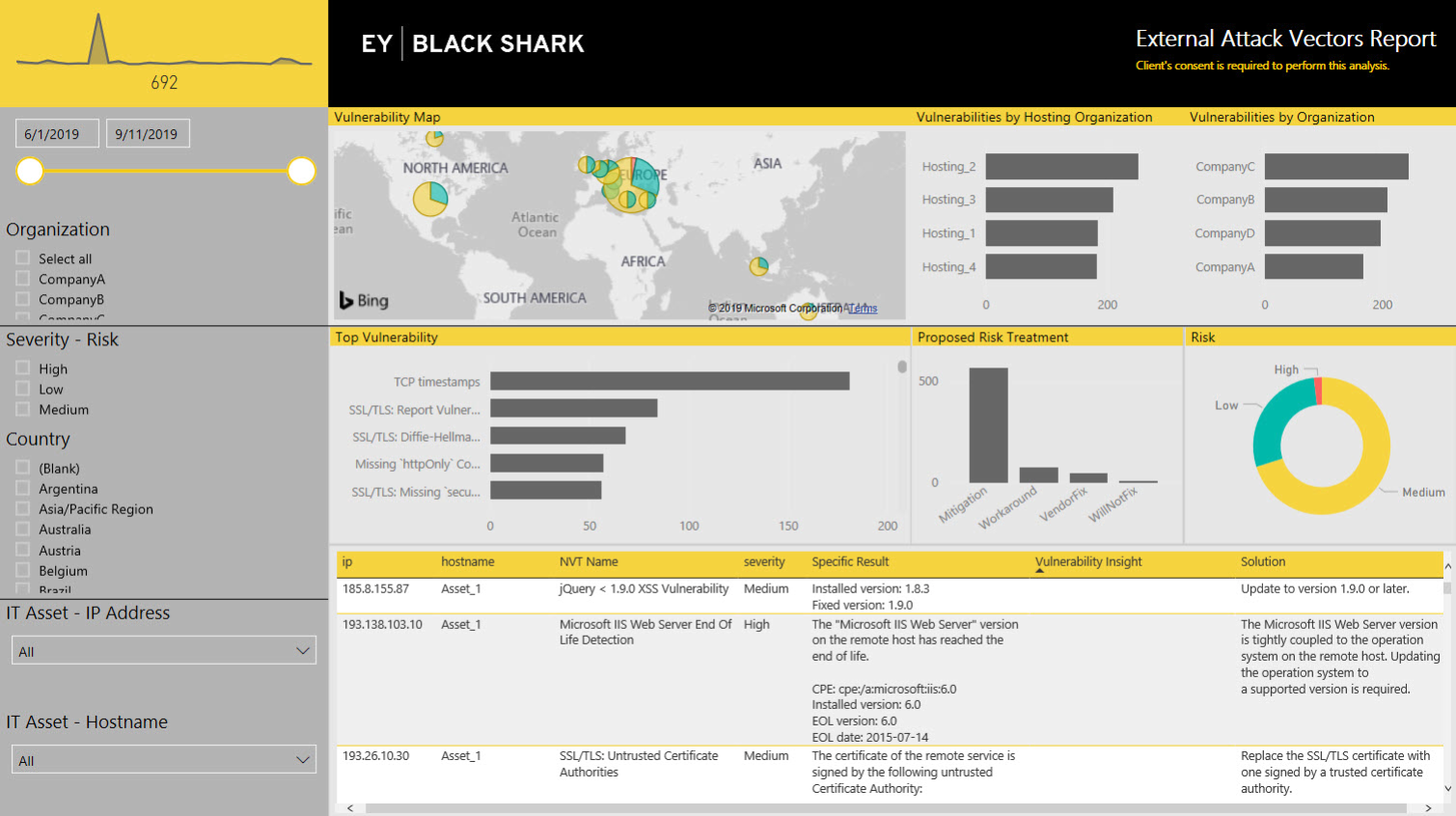
- Vulnerability Map
- Top Vulnerabilities
- Proposed Risk Treatment
- Risk Intensity
An interactive dashboard displaying exposed professional email addresses of the organization’s employees on the internet and if they were part of publicly disclosed data breaches.
A significant number (77%) of organizations are still operating with only limited cybersecurity and resilience. They may not even have a clear picture of what and where their most critical information and assets are — nor have adequate safeguards to protect these assets.
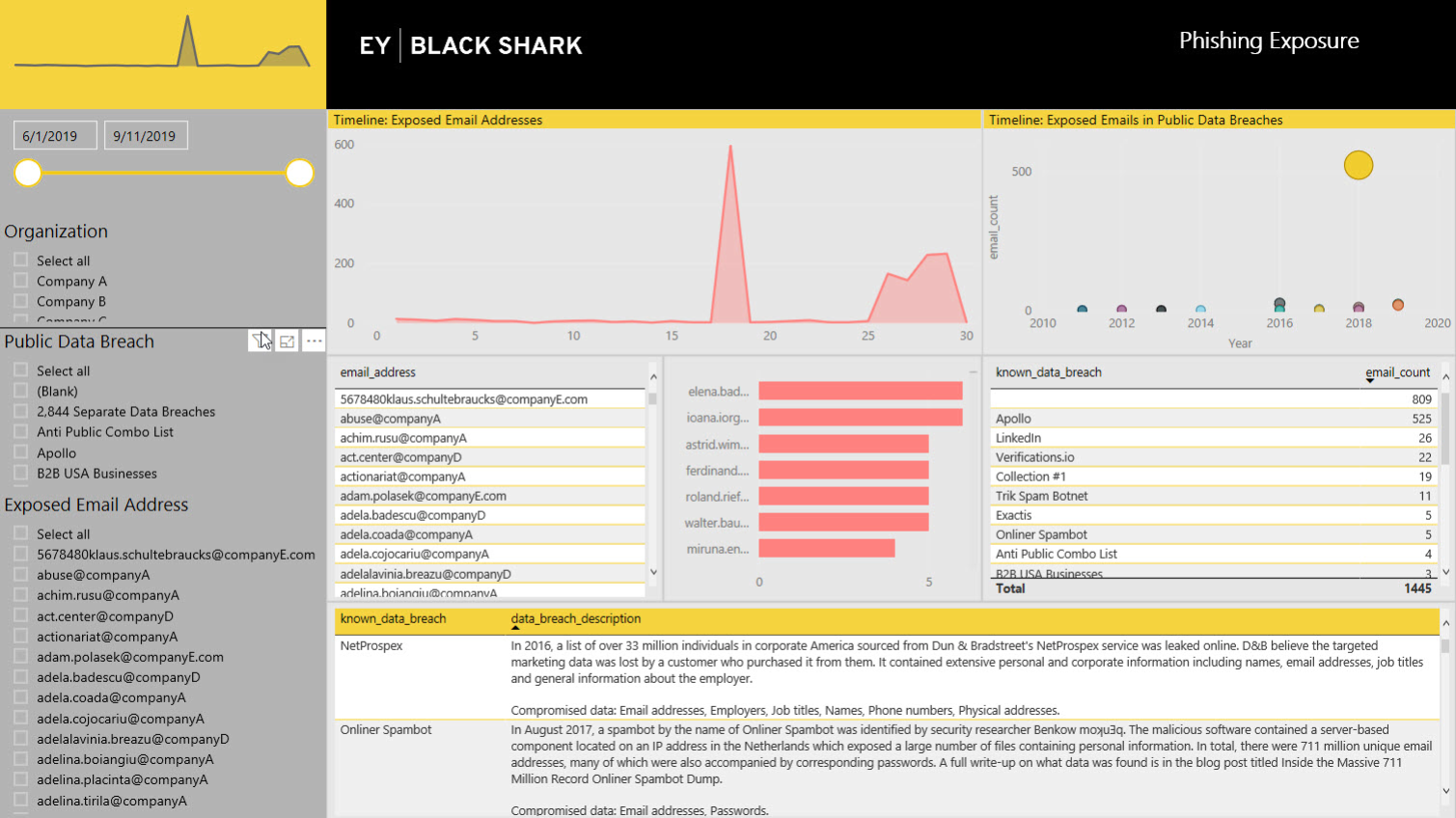
- Timeline of exposed email addresses
- Timeline of exposed emails in Public
- Data Breaches
- Known Data Breach listing
- Data Breach Description
EY BlackShark – What it is
EY BlackShark is a cyber intelligence service that takes an adversarial approach to identify and assess the security posture of the external IT assets of an organization. It uses (not simulates) the same TTP’s (tools, techniques, procedures) of complex cyber threats in order to map the entire attack surface of a target organization and to identify any weak points that can be attacked in order to gain access to data and internal assets. Like any complex adversary EY BlackShark uses techniques to identify the active employees of the target organization for possible social engineering and phishing attacks. If the security posture of the organization is strong EY BlackShark will identify and assess any third parties, vendors, suppliers who have a cyber interaction with the target organization in order to identify other attack vectors.
The amount lost by a businessman in a scam combining "catphishing" and "whailng"
$ 729,000Dark Reading, 26 April 2018. [https://www.google.co.uk/search?q=New+Phishing+Attack+Targets+550M+Email+Users+Worldwide&oq=New+Phishing+Attack+ Targets+550M+Email+Users+Worldwide&aqs=chrome..69i57.363j0j4&sourceid=chrome&ie=UTF-8]
EY BlackShark consulting services
Using the unique expertise of the team behind EY BlackShark, existing clients can access specific tailored services including:
- Cyber interdiction support (proactive and active defence)
- Cyber forensics and incident response including malware reverse engineering
- Cyber vulnerability research and exploit discovery
Benefits
- Visibility across the entire external IT ecosystem
- using OSINT and SIGINT techniques
- Discovery of vulnerable assets and IT equipment
- exposed on the Internet
- Data breach discovery
- Exposure to phishing attacks
- Third party cyber risk management
- Third party due diligence
- Threat hunting intelligence
- Incident response support
Key differentiators
- MONTLHY SUBSCRIPTION PRICING
- 24/7 ACCESS THROUGH EY CLOUD PORTAL
- AGENTLESS DESIGN
- NO IMPLEMENTATION COSTS
- NO MAINTENANCE FEES
- DELIVERED SERVICES ARE IN COMPLIANCE WITH ASF-NORM 4, BNR-R NO.3, EU-GDPR, EU-NIS and TIBER-EU
Additional Services
- Cybersecurity Vulnerability Assessment
- Remote and mobile workforce cybersecurity assessment
- Vital business processes cyber resilience assessment
- IAM Program Assessment
- Incident response program assessment
- DFIR - Incident Response and Digital Forensics support
- Cybersecurity crisis response in case of malware outbreaks (ransomware and other threats)
- Cyberspace active monitoring to identify potential threats like phishing and spam, impersonation and fake news impacting the organization
- Threat Hunting Services
- Support for proactive defense (Cyber Interdiction)
- Pandemic outbreak resilience assessment
- Pandemic emergency planning review
- Crisis management preparedness review
- Cyber capacity management assessment


