Chapter 1
Disruptive technologies at work
Developing intelligent infrastructure through gathered insights
Governments have harnessed disruptive technologies to improve decision making and enhance efficiency while reducing challenges. The primary benefits include the development of intelligent infrastructure through gathered insights. There are three primary technologies impacting smart cities:
- Internet of things (IoT) and sensors: These sensor based technologies gather data which is analyzed for transformative digital implementations. The increased cloud computing usage has led to an increased number of entry points for cyber attackers. Governments must consider data protection politics, defense approaches and security solutions to mitigate risk.
- Connected cars: Automotive suppliers face challenges with respect to protections for connected and autonomous vehicles due to lack of regulations. A Security by Design approach would require standardizations and minimum security requirements for manufacturers to implement.
- Smart meter and smart grid: These predictive technologies collect large amounts of data through partnerships and need to be protected. Detective, preventative and reformative measures need to be integrated alongside government regulatory frameworks, policies and procedures to help to digitally transform the power infrastructures.
Chapter 2
Security challenges and solutions
Exploring innovative strategies to make up for outdated technologies
To ensure sustainable development of smart cities and overcome the challenges of antiquated infrastructure during the rapid urbanization, cities must rethink their innovative strategies to counterbalance outdated technologies.
Estimated cities
66Will have between 5 and 10 million inhabitants by 2030.
Eight core security challenges have been identified for the consideration of cities across Africa and the Middle Eastern regions:
- Insecure hardware: a lack of testing and standardization has let to vulnerabilities to cyber attacks and signal failures.
- Linking vision with strategy and policy: a misalignment between strategies, policies and regulations and the vision for smart cities.
- Multiple implementation programs: numerous initiatives running in parallel leads to the prioritization of solving logistical challenges and a lack of attention on security vulnerabilities.
- Larger attack surface: an increased number of potential entry points for hackers due to the large number of individual devices connected to the network.
- Inadequate funding and finance: cities often compensate for reduced budgets by decreasing cybersecurity budgets in favor of large-scale technology investments.
- Lack of standardized security architecture: a lack of standardization and communication between city systems and security controls.
- Operational Technology (OT) infrastructure security controls: an OT infrastructure that is administered by a generic IT infrastructure.
- Deployment of disruptive technologies: a lack of practicality and cost-benefit analysis in adopting disruptive technologies.
Governments need to take an active role in the urbanization and transformation of cities and embed a Security by Design approach into their smart city transformation and technology implementations to reduce the risk of cyber attacks.
They must also establish responsible committees, security initiatives and a multifaceted defense-in-depth approach to protect connected devices while taking note of the potential challenges. In order to develop sustainably, governments must also factor in costs and security architecture design to account for rapid urbanization.
Chapter 3
Cybersecurity trends
Knowing the trends to stay one step ahead
EY researchers identified thirteen trends that may pose a challenge to the infrastructure of a smart city:
- IT infrastructure improvement
- Rise of megacities
- Demographic shift
- Technology implementations
- IoT
- Carbon removal solutions
- Cybersecurity expertise
- Harmonization
- Crown jewel identification
- Cybersecurity program refresh
- Computer emergency response
- Laws and regulations
- Agile operating model
The most staggering trend is the discrepancy between cybersecurity implementation and smart city digital adoption. According to the IMD Smart City Index Report 2020, security is not considered a priority for top-ranking smart cities, an initiative that should otherwise be inseparable from smart city developments.
Chapter 4
Cyber threat landscape
Understanding the entirety of potential and identified cyberthreats
Almost half of corporate boards believe that cyber attacks will harm their business over the next 12 months. In order for smart cities to develop their cybersecurity, they must first understand the threat and risk landscape.

Governments and authorities must consider the types of threats and potential impacts of the attacks and proactively assess and account for cybersecurity safeguards. The EY report identifies three categories of cyber attacks on governments.
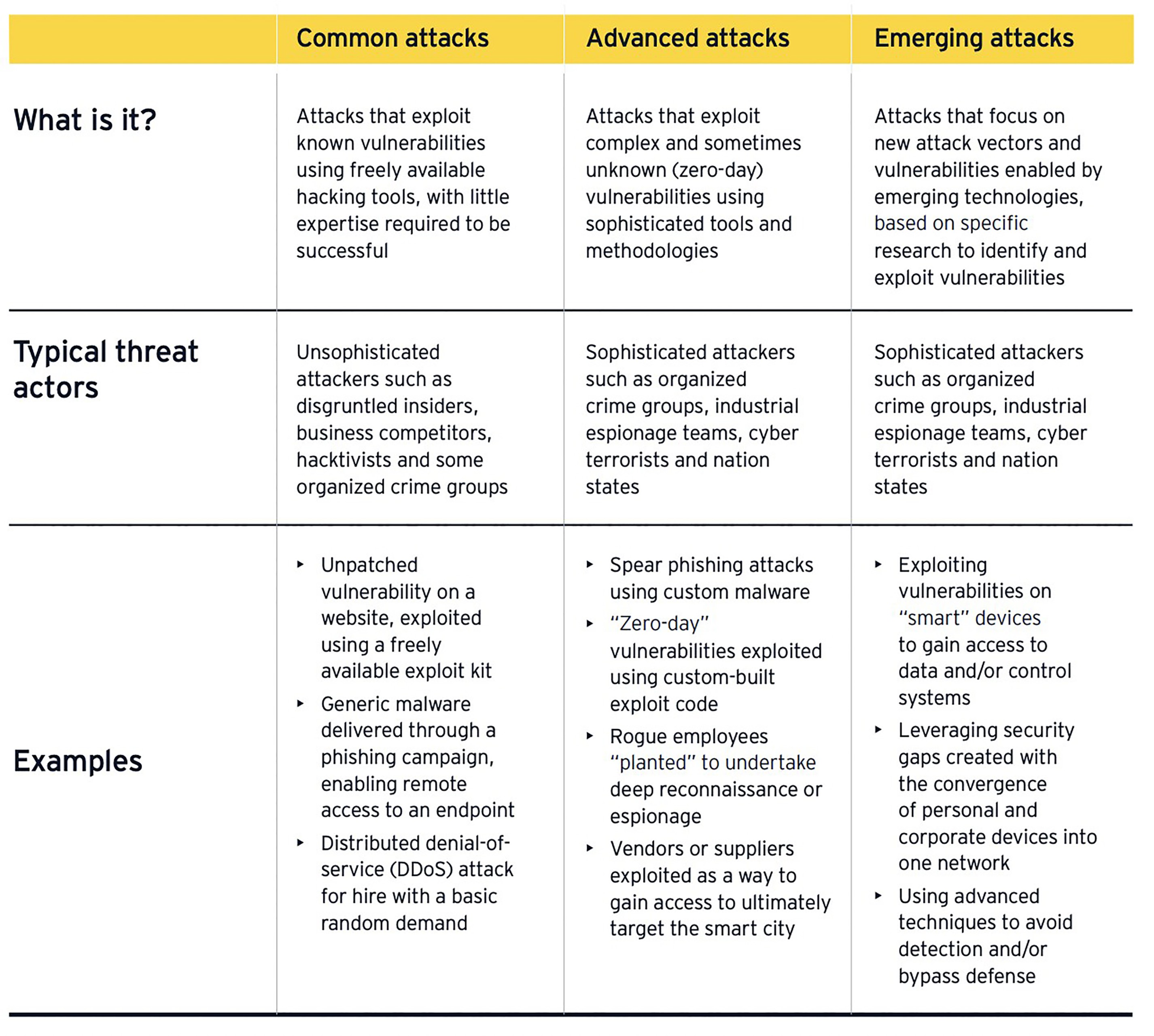
Chapter 5
Key considerations for governments
Toward safer and sustainable new infrastructures
As new technologies are adopted and smart cities utilize more interconnected systems with single data consolidations, new procedures and regulations are required to ensure the safety and sustainability of new infrastructures.
Governments must account for seven key considerations to maintain a resilient smart city:
- Interaction and collaboration: the relationship between cybersecurity and other teams and lines of business
- Big data and predictive analytics: considering big data management and the application of security controls to information databases and repositories
- Testing environment: mandating the usage of testbeds across all critical infrastructures and new technology systems
- Security Architecture: creating standards for architecture based on infrastructure networks, data collection, IT platforms, city structure and service offers
- Zero trust and micro segmentation: security procedures to authenticate users and segmentations between cities to mitigate threats
- Physical security: Implementation of security cameras in conjunction with AI technology
- Public-private partnerships: Government support by the private sector to mitigate the challenges of rapid urbanization
Summary
Today, it has become imperative that governments across the world analyze the importance of having an impenetrable cybersecurity system in place, and disseminate cyber awareness to the masses, to thwart any possible attacks. Staying one step ahead of cybercriminals is the need of the hour, as the world stands battered by the COVID-19 pandemic and is forced to rely on the virtual connectivity across all fields and sectors. The governments need to prioritize assets, understand the risk landscape and implement enhanced levels of security control to better manage and mitigate the forthcoming risks.



