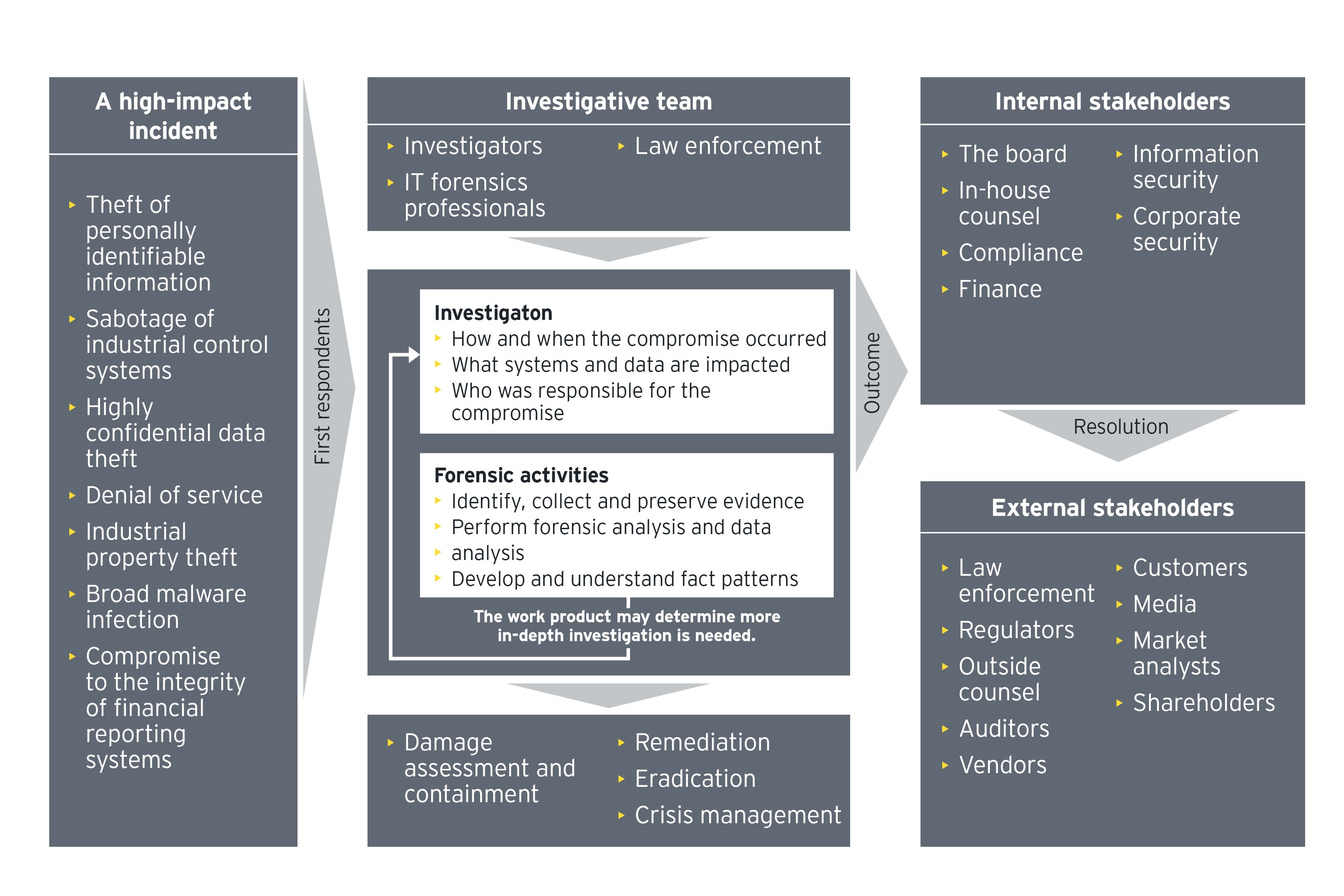
Cyber response consists of a series of stages that must be carefully planned. The plan needs to involve professionals with diverse backgrounds in investigation, information security, legal, regulatory compliance and communication.
Five steps to respond to a crisis
The current threat environment is such that it is only a matter of time before an organization suffers a major cyberattack. Organizations need to have a clear understanding of the key steps of cyber response to be adequately prepared when the crisis strikes. The five steps of cyber response are interdependent and without any sequential order. Performing them in parallel can shorten the time to resolution and reduce risk exposure.
1. Plan
A cyberattack can go undetected for a long period of time. Consistently performing enterprise-wide monitoring and diagnostics is the key to early detection and resolution.
2. Identify and escalate
In this stage, knowledge of the enterprise network environment is critical as the response team isolates the incident and zeroes in on the affected systems and data. Depending on the severity, complexity, and urgency of the incident, appropriate escalation procedures are enacted based on pre-established criteria. The triage guidelines should be continuously fine-tuned to stay current with the organization’s risk environment so that critical risks are not missed, and low-level risks don’t take up precious resources.
3. Investigate
Investigators usually work closely with information security to determine how and when the compromise occurred, the root cause and the impact on the organization. A major incident can involve several cycles of investigation and each cycle includes four key activities: evidence gathering, analysis, containment, and eradication.
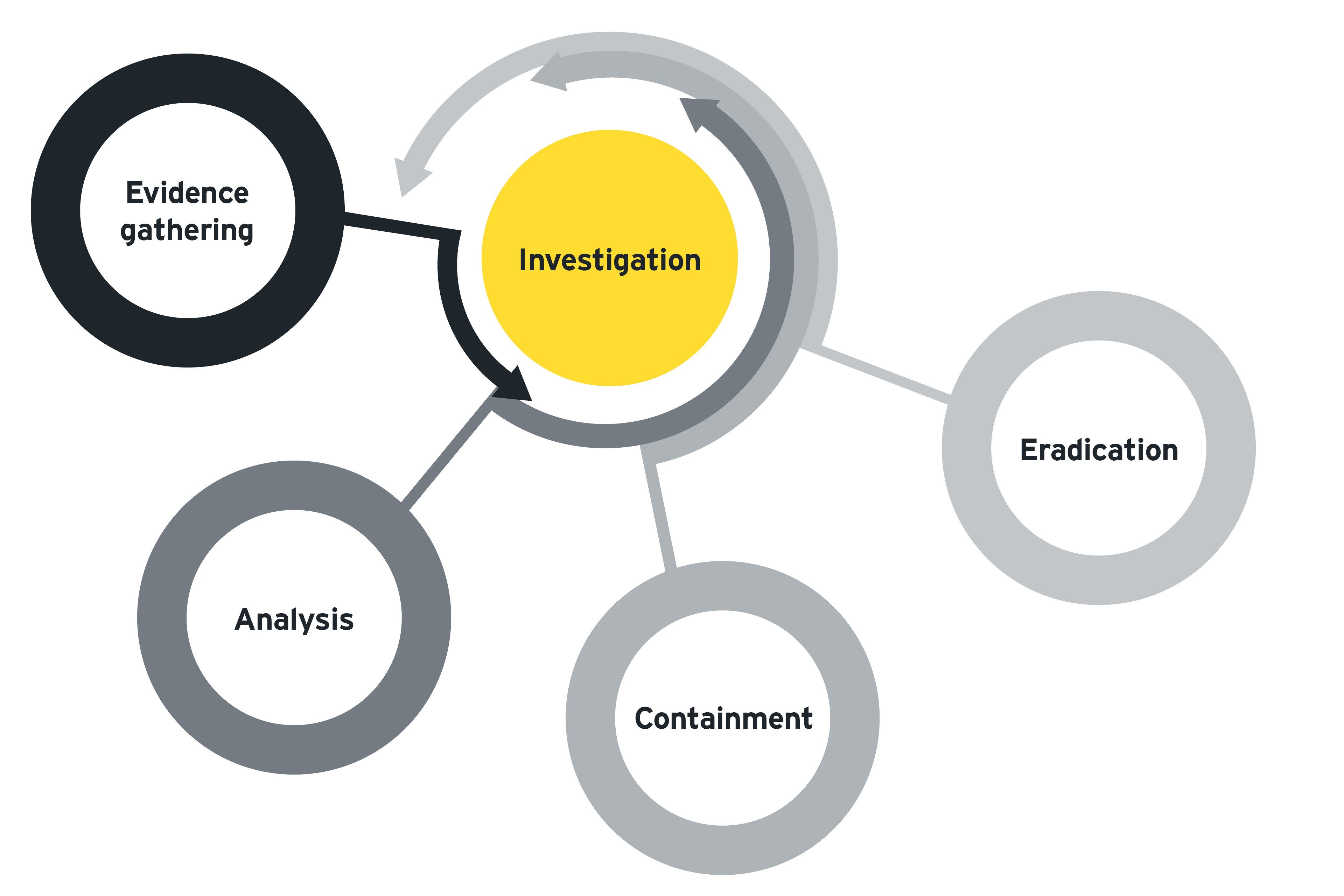
- Evidence gathering needs to be conducted in a forensically sound manner, so findings can stand up to legal and regulatory scrutiny.
- Analysis helps identify the root cause and contaminated computers and systems that should be isolated and removed so the virus doesn’t spread further in the network.
- Containment and eradication could reveal new risks that need to be analyzed further — the cycle of activities will continue until the system is back to its normal state, and all exposed areas have been thoroughly studied and mitigated. All activities must be coordinated and executed with speed and precision, as attackers will often try to re-establish a presence and entrench themselves into the network.
4. Remediate
The compromised organization should identify and address vulnerabilities in the environment, sufficiently strengthen the environment to complicate the attacker’s effort to get back in, enhance its ability to detect and respond to future attacks, and prepare for eradication events.
5. Resolve and learn
This stage largely entails data preparation for regulatory reporting, insurance claims, litigation, threat intelligence and/or customer notification. Beyond reactive activities, it is also important for the organization to turn a reactive crisis management case into lessons for proactive cyber risk management. The cyber response team should summarize information security improvement measures based on the investigation’s outcome.
Cyber response consists of a series of stages that must be carefully planned. The plan needs to involve professionals with diverse backgrounds in investigation, information security, legal, regulatory compliance and communication. The response team needs to be able to mobilize at a moment’s notice and work as a well-oiled machine. In order to do so, they should conduct tabletop exercises on a regular basis to make sure that skill sets are kept up-to-date with the latest threats, and communication links remain operational.
Summary
A well-defined cyber response plan provides guidance to all lines of business involved in the response, sets a level of understanding about what information is critical – as well as when and how to express it – and allows continuous reaction with precision. The plan needs to involve professionals from investigation, information security, legal, regulatory compliance and communication backgrounds with the ability to mobilize at a moment’s notice and work together. To do so, they should make certain that their skill sets are as up to date as possible with the latest threats and communication links remain operational.