EY refers to the global organization, and may refer to one or more, of the member firms of Ernst & Young Global Limited, each of which is a separate legal entity. Ernst & Young Global Limited, a UK company limited by guarantee, does not provide services to clients.
How EY can Help
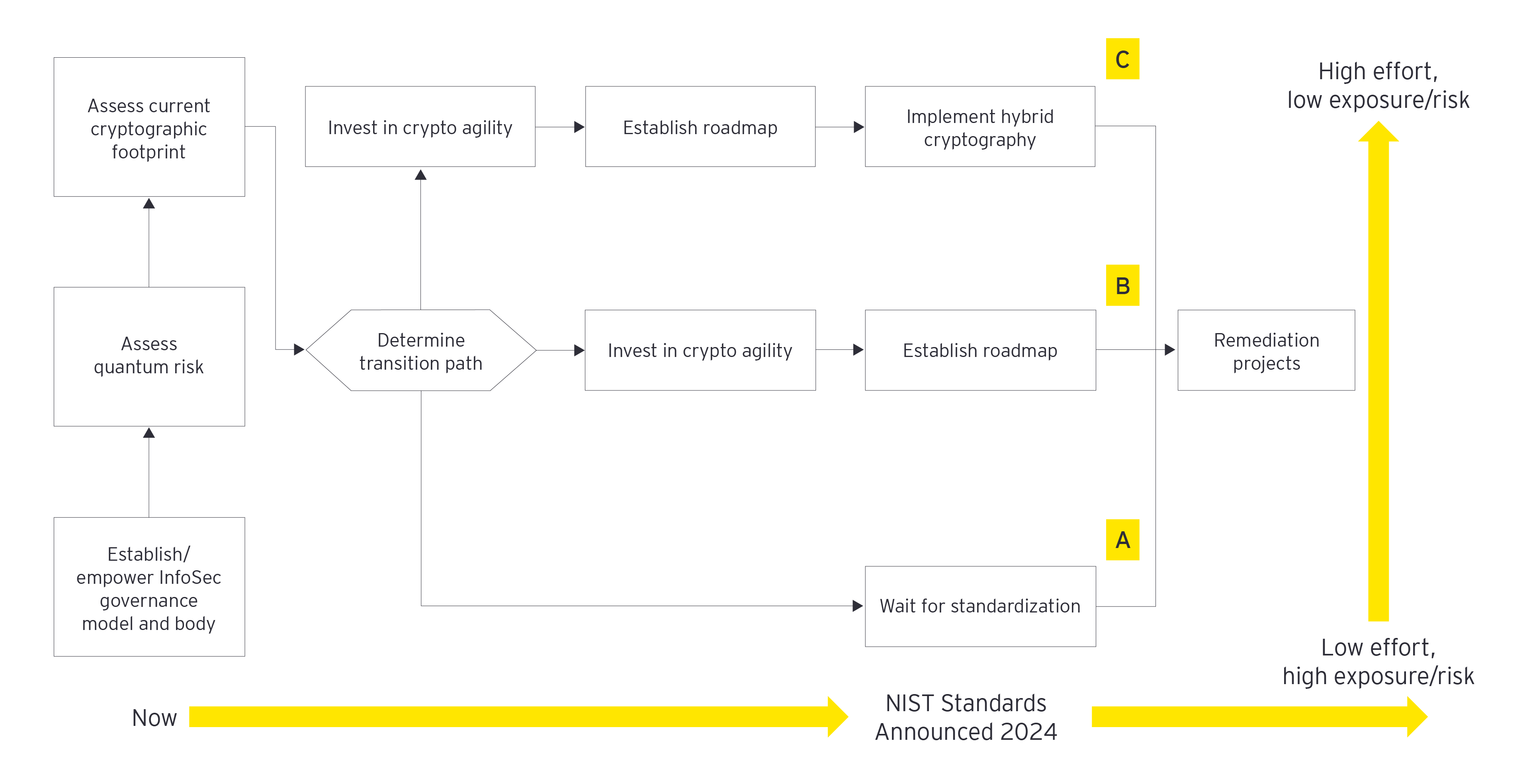
Chief Security Officers (CSOs) can already be formulating a QC strategy that includes:
- Assessing the risks: how much of your encrypted data is at risk?
- Analyzing possible impacts: what would the impact be on your business if this encrypted information was cracked in the next 5-10 years?
- Planning a roadmap: from their current corporate cybersecurity ecosystem to a quantum-powered one — how do we get there from here?
While new QC algorithms will allow businesses to increase their level of security with the inclusion of quantum-resistant cryptography, the security level will also depend on the level of cybersecurity maturity and controls currently in place within the business and the progression of technology in tandem with regulation.
To keep operating successfully and securely, businesses will need to ensure that their quantum-powered cybersecurity plan is fully matured before the threat posed by QC technologies becomes a reality.
To assess the quantum readiness in your cybersecurity business landscape, ask:
- Are data security and encryption essential for your business?
- How well-prepared is your cybersecurity business landscape?
- Are you aware of the cybersecurity threats posed by emerging quantum technology?
- Do you have a full awareness of the risks and threats posed by these technologies?
- Do you have a well-prepared, quantum-powered business model at hand, ready for implementation?
- Are your security protocols “crypto-agile?"
- Can you afford to have sensitive information stolen today to be decrypted when quantum computing technologies are available in the future?