We can and must improve our ability to support senior executives and the board in managing an institution’s cyber risk. We need to move from relying on opinion to using more quantified data to drive decision making. We need to recognise we can model cyber threats via structured scenarios and their associated controls to mitigate these threats. We must understand these models need to take account of both control effectiveness and coverage across the institution’s key assets. We must embrace the data aggregation challenge and make appropriate investments in technology to support this.
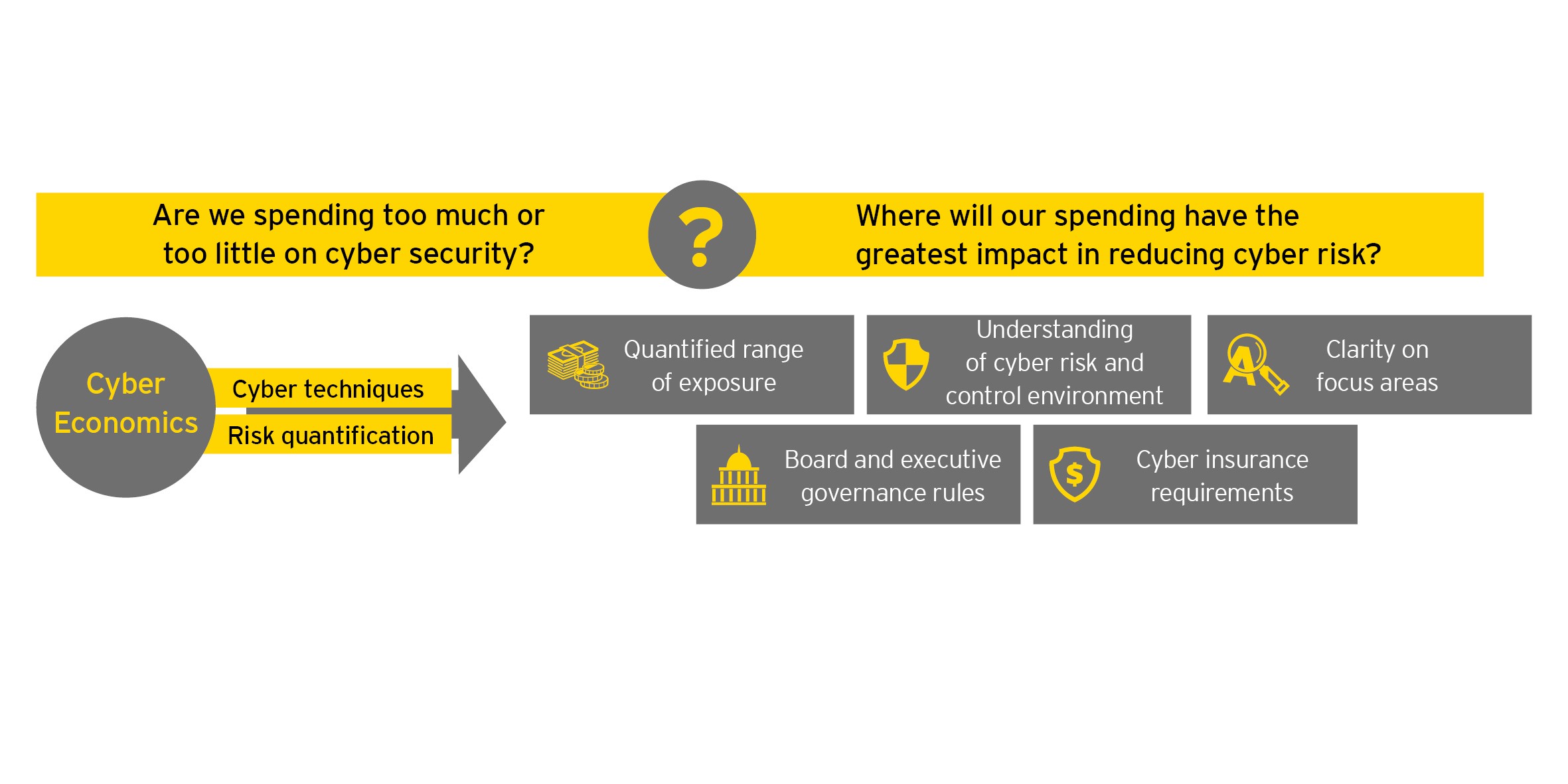
- Develop a top-down model to quantify cyber risk, enabling board and management to understand its quantifiable impacts
- Define metrics and risk indicators that measure the effectiveness and coverage of controls on your key assets
- Connect an integrate data sources to provide the facts to support these metrics
- Automate data collection and use analytics tools to generate and communicate cyber risk insights via dashboards that support the range of views required by various stakeholders, including: executives, board and control owners
- Understand how resilient you are to defend against your key cyber threats
- Identify how much a major cyber incident could cost, how much to spend and how much this will buy down risk
- Improve prioritization by recognizing when further investment provides diminishing returns
- Better forecast when you will return to risk appetite
Summary
Financial institutions are now expected to approach cyber risk decisions in a similar manner to the way they would other risk domains, such as credit risk. The current approach sometimes results in a false sense of security.
Instead they should be using a structured method to asses their strategies through modelling cyber risk within the business value chain, quantifying their risks into business outcomes and ask whether the level of investment is sufficient.
Without a structured, rigorous and data-led approach we will continue to make million dollar investments based on opinions — not facts.


