EY refers to the global organization, and may refer to one or more, of the member firms of Ernst & Young Global Limited, each of which is a separate legal entity. Ernst & Young Global Limited, a UK company limited by guarantee, does not provide services to clients.

The year 2022 is when the judgment of the Court of Justice of the European Union in the Data Protection Commissioner v. Facebook Ireland Ltd and Maximilan Schrems case (the so-called Schrems II judgment) begins to take on a very tangible meaning for all controllers and processors in the Union. Although it has been 2 years since this judgment was issued (the date of the judgment is July 16, 2020), the practical steps to be taken as a consequence of this judgment needed to be taken at the end of 2021 and must be taken in 2022. We are also approaching the very important deadline by which all contracts concluded on standard contractual clauses must be updated to the new model wording issued by the European Commission. The date for the update is December 27, 2022, and agreements of this kind now have to be preceded by an assessment of the transfer's effects on the protection of personal data.
On June 10, 2022, we conducted a webinar on the aforementioned obligations, and asked businesses how much they rate their knowledge and readiness in terms of legally transferring personal data outside the European Economic Area.
The following is a summary of transfer obligations, as well as conclusions from surveys of entrepreneurs.
Despite the complexities introduced by COVID-19, perhaps no issue has been more complicated for privacy pros in recent years than the CJEU’s ruling in the C-311/18 (“Schrems II”) case, which invalidated the EU-U.S. Privacy Shield agreement and drew into question the legality of standard contractual clauses as a means of transferring data outside the European Union.
Indeed, nearly 6 in 10 privacy pros said complying with cross-border data transfer laws is their most difficult task.
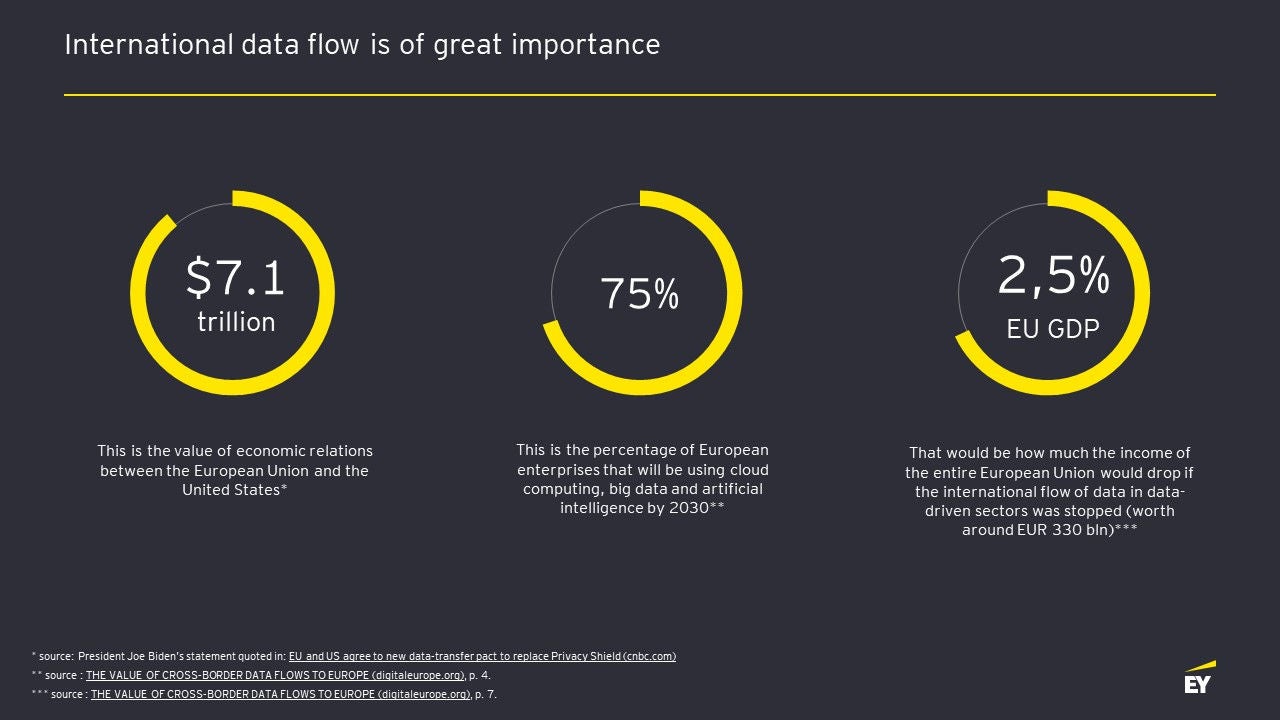
Transfers are of great importance to the Union
The international transfer of personal data is of considerable importance to our convenience, business efficiency, innovation, and profits. One of the most significant data transfers from the European Union is that across the Atlantic, to the United States. According to Eurostat estimates, the economic relationship between the EU and the United States is worth $7.1 trillion. The share of data-driven business will grow in this regard due to gradual technological development and the increasing digitization of more areas of our lives. Eurostat also estimates that if the flow of data outside the European Union in data-driven sectors was stopped - the gross product of the European Union would fall by as much as 2.5%. So, transfers of personal data outside the European Economic Area (EEA) are a necessary part of our everyday life.
Standard contractual clauses - a quick glance on their history
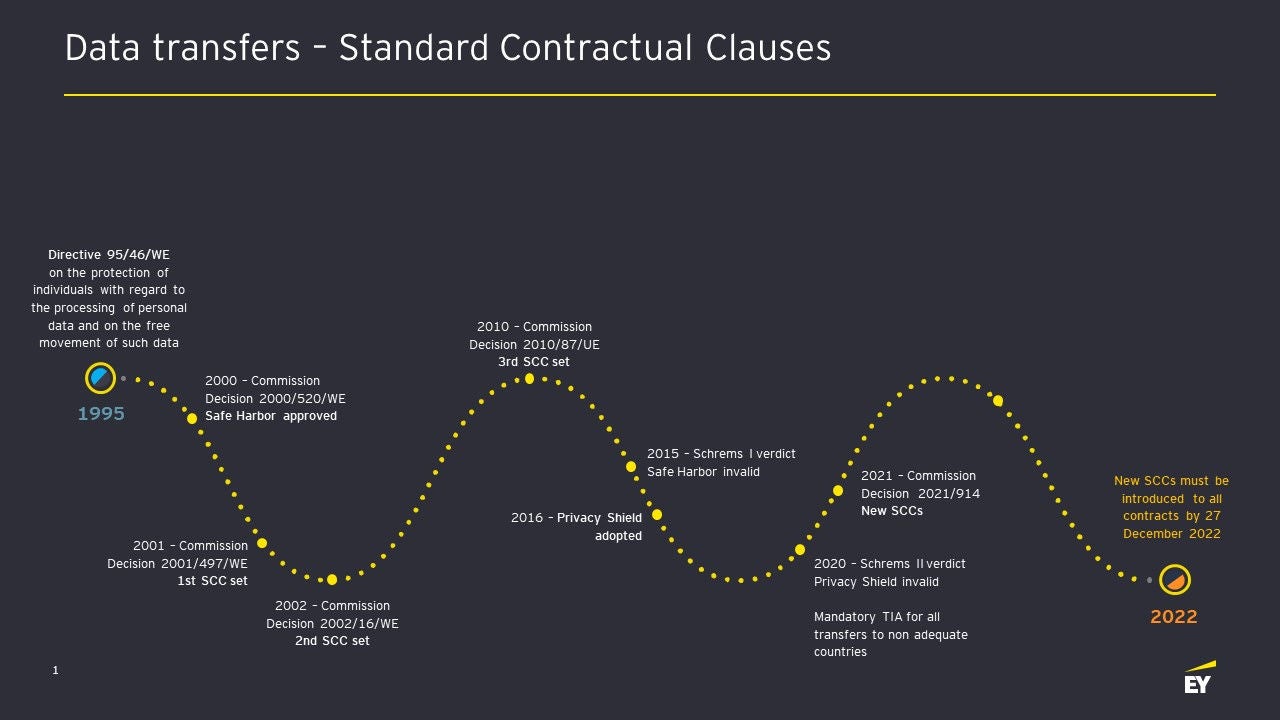
The protection of personal data in the European Union, and thus the controversy over data transfers outside the EEA, did not begin with the entry into force of GDPR. The European Union has already been protecting the personal data of its citizens since 1995 - prior to GDPR, protection was under Directive 95/46/EC (the Directive). It was this Directive that provided for securing data transfers outside the EEA through standard contractual clauses developed by the European Commission.
During the life of the Directive, 3 such sets of clauses were enacted - in 2001, 2002 and 2010. The set of clauses enacted in 2002 expired with the enactment of a new set in 2010.
In addition, while the Directive was in force, the European Commission issued adequacy decisions for third countries regarding the processing of personal data - a mechanism analogous to that under the GDPR. Adequacy decisions issued under the Directive retained their force under the GDPR.
Data transfer to the US
One of the adequacy decisions was the one approving the international agreement between the US and the Union on data transfers - the so-called Safe Harbor (2000). This decision was successfully challenged by Maximilian Schrems in proceedings against Facebook - in 2015 the Court of Justice of the European Union (CJEU) declared this international agreement invalid. The EU and the US quickly drafted and signed a new agreement - Privacy Shield - which was concluded as early as 2016. It was, like Safe Harbor, based on the principle of self-certification of private entities in the US.
Decision 2016/1250 of July 12, 2016, which approved Privacy Shield as an adequate mechanism for securing data transfers between the US and the Union, was declared invalid in the Schrems II ruling. The main objections to the US legal order that led to the overturning of the decision were:
- significant amount of personal data, including metadata, is accessed by US services (e.g., the NSA, CIA and FBI) - including as part of the PRISM and UPSTREAM programs, where personal data on non-US citizens can be extracted from telecom operators' selectors and from cables running on the Atlantic seabed;
- lack of an effective legal remedy against the excessive acquisition of personal data by the services, to which non-US citizens would be entitled.
Comments from a webcast participant
"In my opinion, the problem with personal data in the US does not lie in the issue of authorized institutions requesting access to the data, because in any country, upon request by authorized state bodies, the data will be made available. The problem lies in the uncontrolled access to this data by the services without any information to the data subject or the controller or other data processor. An alternative measure is additional encryption of communications."
At this point, there is still no valid legal basis for the free transfer of data to the US, but talks between the European Union and the US are proceeding rapidly and, it seems, effectively. In March 2022 the European Commission issued a communication indicating that the main tenets of a new agreement to replace Privacy Shield had already been established:
- The agreement is to be based on a similar mechanism to Safe Harbor and Privacy Shield, namely the self-certification of US entities;
- US intelligence authorities are to be bound by safeguards limiting access to the data and ensuring its necessity and adequacy for the purpose of protecting national security; US intelligence services are to adopt a procedure to ensure adequate respect for privacy and other civil liberties;
- A new two-tiered system is to be introduced for handling complaints by Europeans about access to their data by US services;
- Monitoring and verification mechanisms will be put in place.
Comments and questions from webcast participants - in the context of the possibility of limiting data processing in cloud services only to servers in the EEA
Under the US Cloud Act, data processed by US companies is to be provided to authorized authorities regardless of where it is processed. What about the Cloud Act from this perspective, and does regionalization even matter here?
Cloud contracts very often provide service recipients with the option to regionalize services and choose an option in which the cloud provider undertakes to process the service recipient's data only within the EEA. In such a situation, data centers in the EEA are used. Such provisions are recommended to meet the requirements of the GDPR.
In fact, however, the CLOUD Act was passed in the US in 2018, which requires US-based entities to hand over data regardless of where it is currently stored (whether on a server in Europe, for example). According to US lawmakers, such a measure was both consistent with pre-existing US law and was necessitated by the growing number of requests coming into the US from other countries for assistance in obtaining data for prosecutions. Bulk data collection is prohibited under the CLOUD Act.
The CLOUD Act was passed as a result of the Microsoft Corp. v. United States case (about which in a later window).
Ensuring an adequate level of personal data protection in a third country
According to the GDPR (e.g., Article 44), transfers of personal data must be carried out in such a way that the degree of data protection provided by the GDPR is not compromised. This is what the transfer protection mechanisms provided for in Article 46 of the GDPR - including agreements on standard contractual clauses and binding corporate rules - are designed to do.
However, in order for such mechanisms to be an effective way to secure the transfer of personal data to a third country, it is necessary to examine whether they can actually be enforced in the recipient country. After all, as the CJEU noted in the Schrems II judgment - contractual provisions (whether in clauses or binding corporate rules) bind only the parties signing such obligations, but not the authorities in the recipient country. It should also be borne in mind that a data importer, being confronted with a conflict between violating contractual obligations under clauses or binding corporate rules and violating the law in its country of establishment, will in all likelihood choose to violate the contract.
Transfer Impact Assessment (TIA) study for data protection
Both the Court of Justice of the European Union in the Schrems II judgment and the European Data Protection Board, in their post-Schrems II Recommendations 01/2020 on measures to supplement transfer tools in order to comply with the EU's level of personal data protection (version 2.0 adopted June 18, 2021, detailed the elements of a mandatory recipient country assessment that must be conducted before any transfer of personal data to a third country:
- First, it is necessary to accurately map data transfers in the controller's organization. In many cases, this is one of the most difficult parts of the examination. It is important to remember that the check must include not only the contracts that we have actively negotiated with suppliers and that contain a mutually agreed clause mandating that the processor obtains consent for the transfer (and did it actually request it? Also worth checking). It is also necessary to check the tools and services we use based on contracts concluded, for example, on the basis of acceptance of non-negotiable terms and conditions. Issues of transferring personal data to countries such as the US, Australia or other third countries may be part of such provider's terms of service or privacy policy. At this stage, it is also recommended to verify that the transfer complies with the guiding principles of processing like data minimization.
Questions from webinar participants: And what is the issue of using resources (Engineers, Pentesters, etc.) coming from outside the EEA?
Some types of processing are controversial in nature. The European Data Protection Board in Recommendations 01/2020 indicates that providing only access to data to recipients in a third country, even for administrative purposes, will constitute a transfer of personal data to a third country.
On the other hand, Guidance 05/2021 on the relationship between the application of Article 3 and the provisions on international data transfer under Chapter V of the GDPR adopted on November 18, 2021 indicates that if an employee of an EU controller accesses data through the controller's technical means, but while in a third country (e.g., on vacation), this will not constitute a data transfer - because the data is not transferred outside the entity that is the controller - the employee here is seen as part of the organization.
It will also not be a data transfer if the data subject himself/herself provides his/her personal data to a recipient in a third country (e.g., when shopping online).
On the other hand, sharing or entrusting personal data within multinational groups will constitute a transfer of data outside the EEA and requires safeguards.
- Second, it is necessary to verify the legal basis for the transfer. This may be one of the safeguards provided for in Article 46 of the GDPR, but perhaps also an exception provided for in Article 49 of the GDPR (e.g., consent of the data subject). It is important to monitor such safeguards.
In this regard, it is very important to keep in mind that the standard contractual clauses, which are the most popular means of securing data transfers outside the EEA, have changed. They must be updated in existing contracts by December 27, 2022.
Webcast participant's question: please very much refer to data transfer to South Korea
This is a very good example of how important it is to monitor the safeguards in place or applicable. In the case of South Korea, the adequacy discussions ended with a positive decision by the European Commission on South Korea's adequacy in terms of personal data protection. The decision, dated December 17, 2021 (C(2021) 9316 final), approved the possibility of transferring data to South Korea without additional safeguards.
- Third, it is necessary to assess the entire legal system of the country to which we intend to export personal data. Such assessment must include:
- The legal system of the third country in question and whether it is applied in practice (if it would formally meet the European standard) and the relevant elements of practice in the third country in question - including the possibility for European persons to enjoy effective means of protection
- Can public authorities attempt to access data without the knowledge of the data recipient in a third country (in light of current law, practice and precedents)
- Whether public authorities may attempt to access the data through a data recipient in a third country, telecommunications operators or communication channels (in light of applicable law, technical, financial and human capabilities of such authorities)
- The context of data export: the purposes of processing, the nature of the recipient of the data and the relevant sector, the categories of data transferred, where the data will be stored, the format of the data and issues of further transfers.
It is important to remember that while the data exporter may rely on information and assurances obtained from the recipient in a third country, the responsibility to check any publicly available sources - the contents of the law, publicly available decisions, NGO or business reports - remains its responsibility. If the data recipient's statements contradict publicly available information, the responsibility for the unlawful transfer will fall on the data exporter.
- Fourth, if necessary due to problematic legislation or practice in the third country in question, additional safeguards are needed to keep data transfers secure despite such difficulties. Suggested safeguards by the European Data Protection Board include:
- Technical measures: primarily encryption (including in transfer), pseudonymization, separation of processing among several recipients
- Taking advantage of available exceptions in the law of the recipient country - such as statutory professional secrecy obligations
- Additional contractual obligations: to list any applicable regulations, to provide information on data release requests received, including statistics relating to the past, measures taken to prevent disclosure of data, no obligation to leave workarounds for authorities, to provide no-request reports (Warrant Canary), to use all remedies to challenge data release, to inform the data subject of a data release request, to support the data subject against public authorities.
- Organizational safeguards at the third-country data recipient: delineating clear roles and responsibilities, including the organization's response to a request for data received from a public authority; records of requests and responses made available to the exporter; ensuring a strict approach to data access (on a need-to-know basis), adherence to these principles, regular auditing and implementation, including through disciplinary measures.
It is worth mentioning that one of the additional safeguards for the transfer of personal data to a third country is the obligation of the recipient to take all procedural steps available under local law to challenge a request by administrative authorities or services for access to data.
This was the situation in the case of Microsoft Corp. V. United States from 2018. In that case, Microsoft sought to win the right to deny access to its service recipients' data, which was stored on Microsoft servers in Ireland, before the US courts. The case went all the way to the Supreme Court, where Microsoft came close to winning (a win was prevented by the passage of the CLOUD Act, which we write about in the earlier box).
- Fifth, you should take the steps necessary to ensure that the security method you apply is valid. It may be that the modified contractual clauses you have applied, for example, will require confirmation by the relevant supervisory authority.
- Sixth, it is necessary to ensure regular repetition of the entire procedure for assessing the impact of the transfer on data protection, because the risks, as well as the safeguards in place change and outdate, while the high standard of personal data protection required by the European Union does not diminish.
Need to update clauses
As we mention above, sets of standard contractual clauses that were adopted before 2021 are gradually becoming obsolete. Starting as early as the fall of 2021, they should not be used for new contracts, and as of December 27, 2022, they should be updated to the new model adopted by Commission Decision 2021/914 of June 4, 2021.
There were several reasons for updating the sets of standard contractual clauses:
· The clauses adopted in 2001 and 2010 (i.e., those still in force until 2021) were drafted at a time when the applicable EU data protection legislation was still Directive 95/46/EC - while as of 2018, GDPR is in force and introduces new obligations;
· The clauses were drafted more than a decade ago in a different reality than the one we face today. It was necessary to ensure that the sets of clauses enabled both the correct reflection of factual situations - long chains of processing and onward entrustment of data, transfers between processors or controllers in different countries, as well as enabling clauses between more than two entities and the dynamic accession of additional entities to the agreements.
The new standard contractual clauses are based on a modular system that allows the selection of contractual elements that are most appropriate for the actual relationship between the parties. This is intended to provide more practical data protection in transfers outside the EEA.
Direct at your mail
Subscribe EY newsletters
Summary
The year 2022 is when the judgment of the Court of Justice of the European Union in the Data Protection Commissioner v. Facebook Ireland Ltd and Maximilan Schrems case (the so-called Schrems II judgment) begins to take on a very tangible meaning for all controllers and processors in the Union. We are approaching the very important deadline by which all contracts concluded on standard contractual clauses must be updated to the new model wording issued by the European Commission. The date for the update is December 27, 2022, and agreements of this kind now have to be preceded by an assessment of the transfer's effects on the protection of personal data.
Related articles
Security on the Internet. New European initiative – digital services act
Digital Services Act (referred to as „DSA”) was adopted as part of the European data strategy presented by the European Commission ("EC") in February 2020.
The German Packaging Act and new obligations for Polish companies
All traders who have supplied packaged goods to and from the end consumer in Germany are required to register with the LUCID Central Register of Packaging.





