Cybersecurity failure is one of the risks that worsened the most through COVID-19.
Focus on boards
Boards are taking an increasingly active role in addressing cybersecurity risks posed to their businesses. There is an increasing demand on management to generate reporting, metrics and insight that provide visibility and assurance over the management of cybersecurity risks.
Most organizations struggle with understanding what to report to the board. This is indicative of the traditional reporting mindset that tends to focus on informing tactical decision-making and reporting on current progress. Instead, board reporting should seek to combine tangible and quantifiable metrics that demonstrate the outcomes resulting from recent key decisions and the performance of the current control environment.
Ultimately, to enable effective decision-making, a successful cybersecurity reporting framework must provide the board with a clear and continuous view of the organization’s current cyber risk exposure.
To encourage this paradigm shift, boards should apply a risk-focused mindset to transform the questions they ask of management.
Call to action for CISOs
- Firstly, start to prepare for a “modern” enterprise-wide security architecture, as the next five years will inevitably see significant shifts in technology and data; especially as there is accelerated adoption of cloud, analytics and automation across the sector, as well as disruptive innovation to achieve decarbonization targets
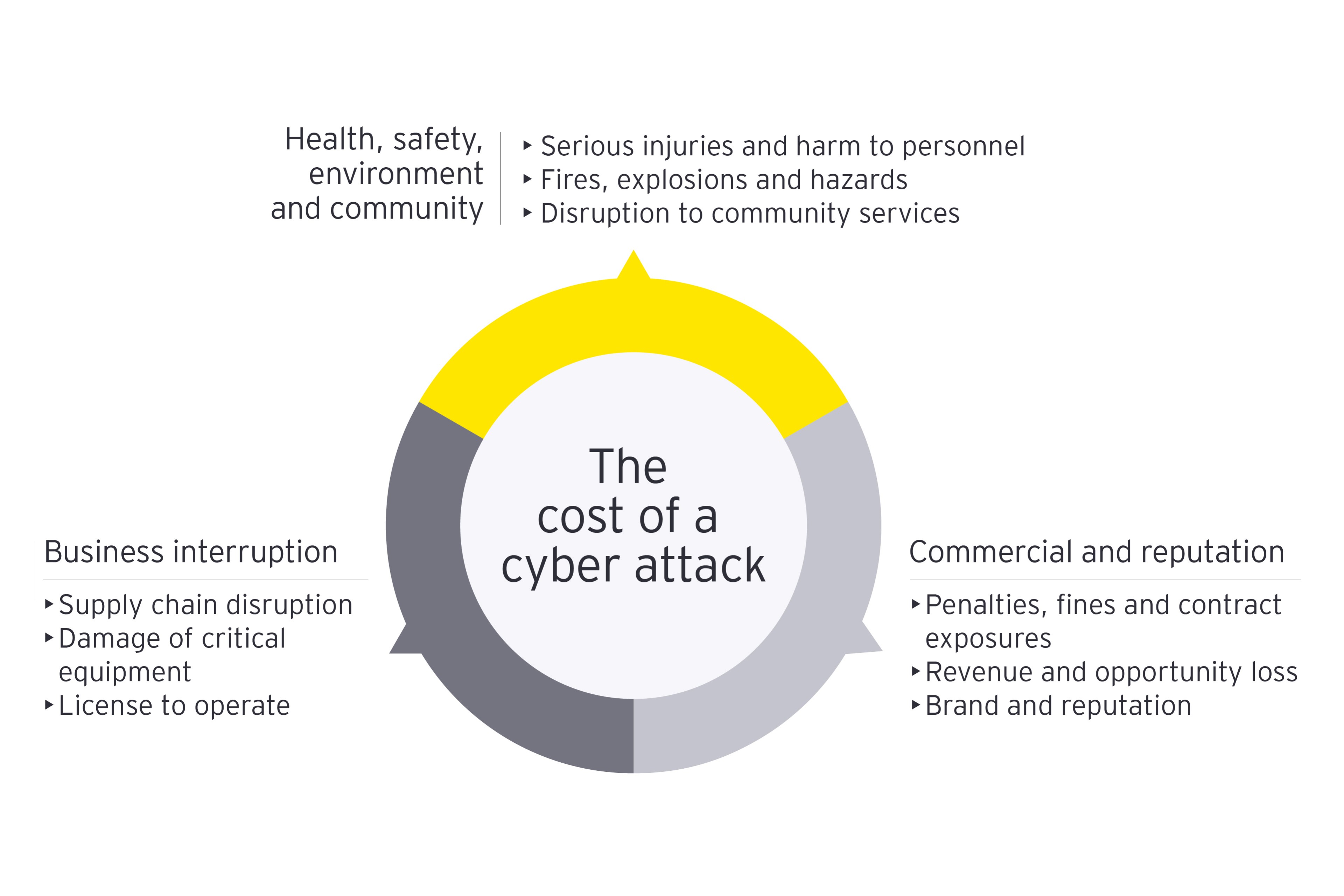
- Raise the profile of cyber as a strategic imperative to deal with potential business interruption, safety and financial impact due to the rise of financial cybercrime (ransomware as a service), critical infrastructure protection (regulatory) and changes to ways of working
- Communicate using the enterprise risk framework to help build trust and enable a common language, and consider linking OT cybersecurity to safety or financial value to help articulate the risk
- Seek opportunities to reset cybersecurity foundations, such as identity and access management and zero trust security architecture, as part of broader ERP modernization and digital transformation programs
- Develop and implement better governance: through standardizing cyber, by applying control assurance practices. These will confirm the coverage and effectiveness of the collective cyber controls and manage the key cyber risk scenarios
Summary
Cyber risk can be the downfall of a mining and metals organization’s productivity gains and digital aspirations. And the cost of these attacks is climbing steeply. According to the latest EY Global Information Security Survey (GISS), 71% of the respondents have seen an increase in the number of disruptive attacks over the past 12 months.