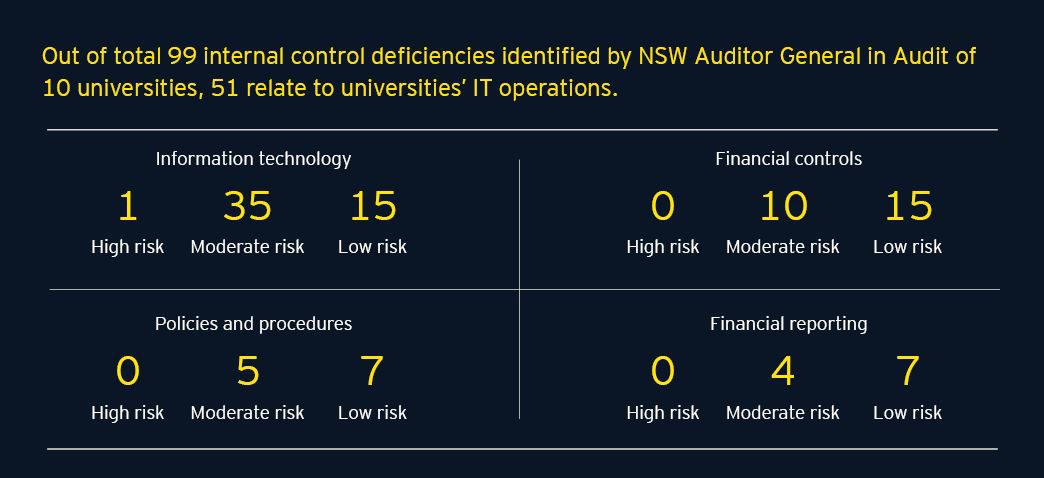
There is a focus on increasing cyber regulatory measures to protect education institutions. Poor IT controls increase the risk of inappropriate access, cyber security attacks, data manipulation and misuse of information security policies, so it is important to understand these organisational weaknesses.
Five guiding principles
1. Protect what matters most
In an environment such as the education sector where there is so much to protect, leadership must focus on securing the information and assets that have the biggest impact on their business’ mission.
2. Manage cybersecurity risk at the right level
Confirm that the institution takes a whole-of-organisation approach to cyber security, with operating units understanding their roles.
3. Provide the right access at the right time
By simplifying access processes for the user base, educational institutions can provide a better user experience and more easily identify unauthorised users.
4. Recover quickly and securely
From IT professionals with hands on keyboards to the university’s senior management and Senate, it is essential that educational institutions know what to do when a cyber incident occurs.
5. Practice proactive cyber security
Proactive security combines traditional security defences and a strong security foundation with realtime monitoring and intelligence-led data to predict security events.
Find out about more about a cyber security approach for leadership in education.
Summary
When it comes to network compromise, it is no longer a question of if, but when. At its core, cyber security seeks to reduce vulnerabilities and build capacity to identify and respond to these incidents. Although a cyber security program cannot guarantee absolute security, it will provide the capability to manage the impact of such malicious cyber incidents and enable the reduction of harm to reputation, manage the impact of such malicious cyber incidents and reduce the reputational harm to the institution due to the compromise of the confidentiality, integrity, or availability of systems or data.



