The implementation of the new 2021 SWIFT CSP requirements can be very challenging, as it not only impacts SWIFT members but also the ITOs and BPOs that support them.
Understanding SWIFT architecture types and the CSP assessment
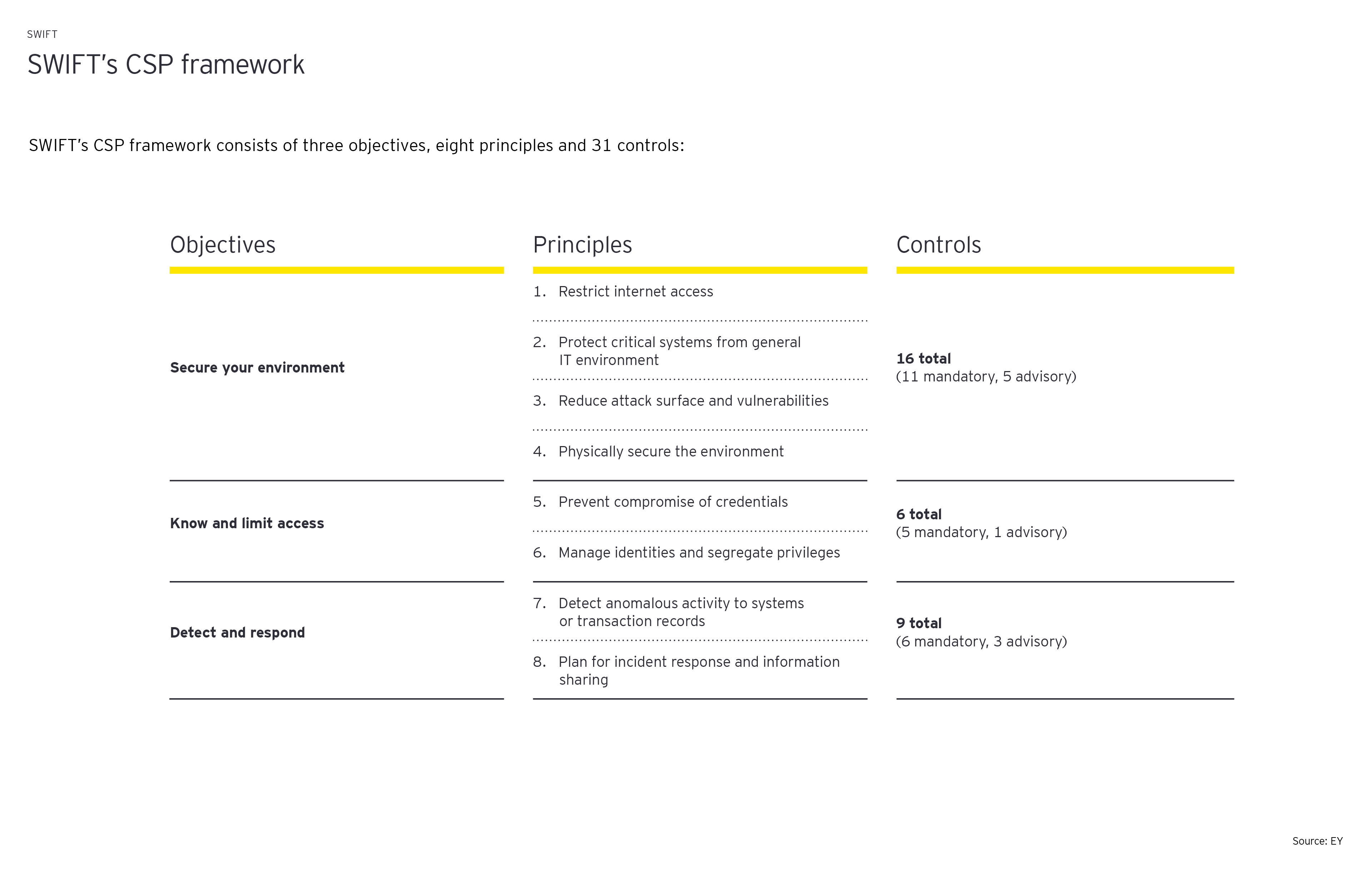
The SWIFT 2021 assessment comprises a maximum of 22 mandatory and nine advisory controls with comprehensive implementation guidelines. The total number of controls is determined by the “SWIFT architecture type”, defined by how SWIFT members connect the SWIFT network. SWIFT distinguishes between five possible architecture types (types A1-A4 and type B) with all 31 controls in scope for architecture types A1 and A2, and only a subset of 22 controls in scope for architecture type B.
Implementation of SWIFT CSP requirements tends to be challenging
An increasingly number of SWIFT members have outsourced part of their IT infrastructure and/or business processes to IT Outsourcing (ITO) and Business Process Outsourcing (BPO) providers. However, the ultimate responsibility for SWIFT CSP compliance remains with SWIFT members (namely, the organizations that own the SWIFT Business Identifier Code (BIC)). Therefore, increasingly more SWIFT members expect to receive SWIFT CSP compliance assurance reports (e.g. ISAE 3000 reports) from their ITOs and BPOs. As such, it is not only the SWIFT members but also ITOs and BPOs that support them, that need to prepare for compliance with the new requirements in 2021.
The implementation of the SWIFT CSP requires time, know-how and resources, and can be complex and challenging. The following six steps are crucial for SWIFT members as well as ITO and BPO providers:
- Set up a cross-functional team to oversee implementation, including IT, risk and compliance
- Analyze past IT and information security audits to identify critical gaps which need to be addressed as part of the SWIFT CSP implementation project
- Conduct readiness assessments for mandatory and advisory controls
- Evaluate to what extent SWIFT CSP control requirements can be automated by technological solutions (e.g. continuous monitoring of SWIFT logs regarding possible anomalies) instead of purely manually driven control activities
- Understand how the implementation of the SWIFT CSP can be aligned with broader cybersecurity initiatives
- Determine the extent to which existing ISAE 3000 or similar Service Organization Control reports are already addressing SWIFT CSP controls to understand what needs to be in place in addition
The pressure is on
SWIFT members are required to submit their SWIFT CSP attestation based on an independent SWIFT CSP assessment report by 31 December 2021. The pressure is on, and there’s no time to waste to kick off planning as early as Q1 2021.
The consequences for non-compliance are high. If a SWIFT member fails to comply, SWIFT will inform other SWIFT members and may report deficiencies to local supervisory authorities in the respective operating countries of those members. Not only can this directly jeopardize business operations, but it may incur untold reputational damage and stakeholder trust. On the other hand, proactive planning and a reliable delivery provider of the necessary assessments will help organizations to remain focused on their primary cybersecurity mandate without compromising on critical compliance.
Summary
Member organizations of the SWIFT network are required to submit their SWIFT CSP attestation by 31 December 2021 based on an independent assessment. The pressure is now on CISOs to plan for and undertake the necessary steps for compliance. This can be both complex and time consuming if not well planned and executed.


