Organizations today must innovate to survive, but in doing so face ever-growing threats of cyber-attacks and increased regulatory pressure
For many years, the financial industry has been seeking ways to assess their current cyber situation rapidly as the basis for developing agile strategies and roadmaps for transformation. To address their risks, they need to consider complex, interrelated aspects such as cybersecurity, supply chain, finance, IT and other business areas. Until now, the market has struggled to provide adequate tools that truly enable organizations to address these challenges. Those available tended to lack an efficient assessment lifecycle (e.g. not providing an end-to-end solution) or fell short on deep insights. In the absence of benchmarking data for comparisons with peers, sectors or the industry as a whole, decisions have often been constrained by internal data. This limited visibility was often paired with the absence of an evidence-based approach, resulting in a poorer quality decision-making basis. This was reflected in our latest EY Global Information Security Survey (GISS) where an overwhelming majority of Swiss participants confirmed that they have little trust in cyber risk measures presented to them.
Lack of trust
20%of boards are confident that the cyber risks and mitigation measures presented to them can protect their enterprise from cyber-attacks
A holistic and fit-for-the-organization assessment starts by identifying relevant risk scenarios. As organizations continue to evolve and adapt to the ever-changing economic, threat, regulatory and technology landscapes, they are likely to be faced with one or a combination of the following scenarios:
Once one or more of these risk scenarios have been identified, it is also wise to maximize the potential value from these unique opportunities (e.g., when a new cybersecurity leader takes over the cybersecurity function).
The role of Chief Information Security Officers (CISOs) in Switzerland and across Europe is shifting. No longer seen as innovation blockers, today’s CISOs are problem solvers who enable their organizations to transform safely and securely. Especially in today’s world of constant change, organizations need to assess capabilities continually to stay relevant and gain a competitive advantage. They need to confront unforeseen situations and be prepared well in advance to handle situations in a volatile, uncertain, complex and ambiguous (VUCA) environment. To align efforts where they are needed most, the strategy should be up to date and able to prioritize focus areas. New value often comes from highlighting issues or topics which might otherwise have gone unnoticed and using them to create opportunities.
CISOs cannot afford to be seen as blockers of innovation; they must be problem solvers — enablers who promote Security by Design and allow their organizations to transform safely and securely
The risk scenarios set out above are also unique opportunities to create value for an organization, by not only further strengthening the cyber controls in place, but by also enabling business functions. To provide better answers and to address the cyber, IT and regulatory challenges outlined, a cyber maturity diagnostic and benchmark assessment can be performed. Such an assessment can help organizations' understanding whether the right information assets are being protected to the appropriate level of security based on their value to the company.
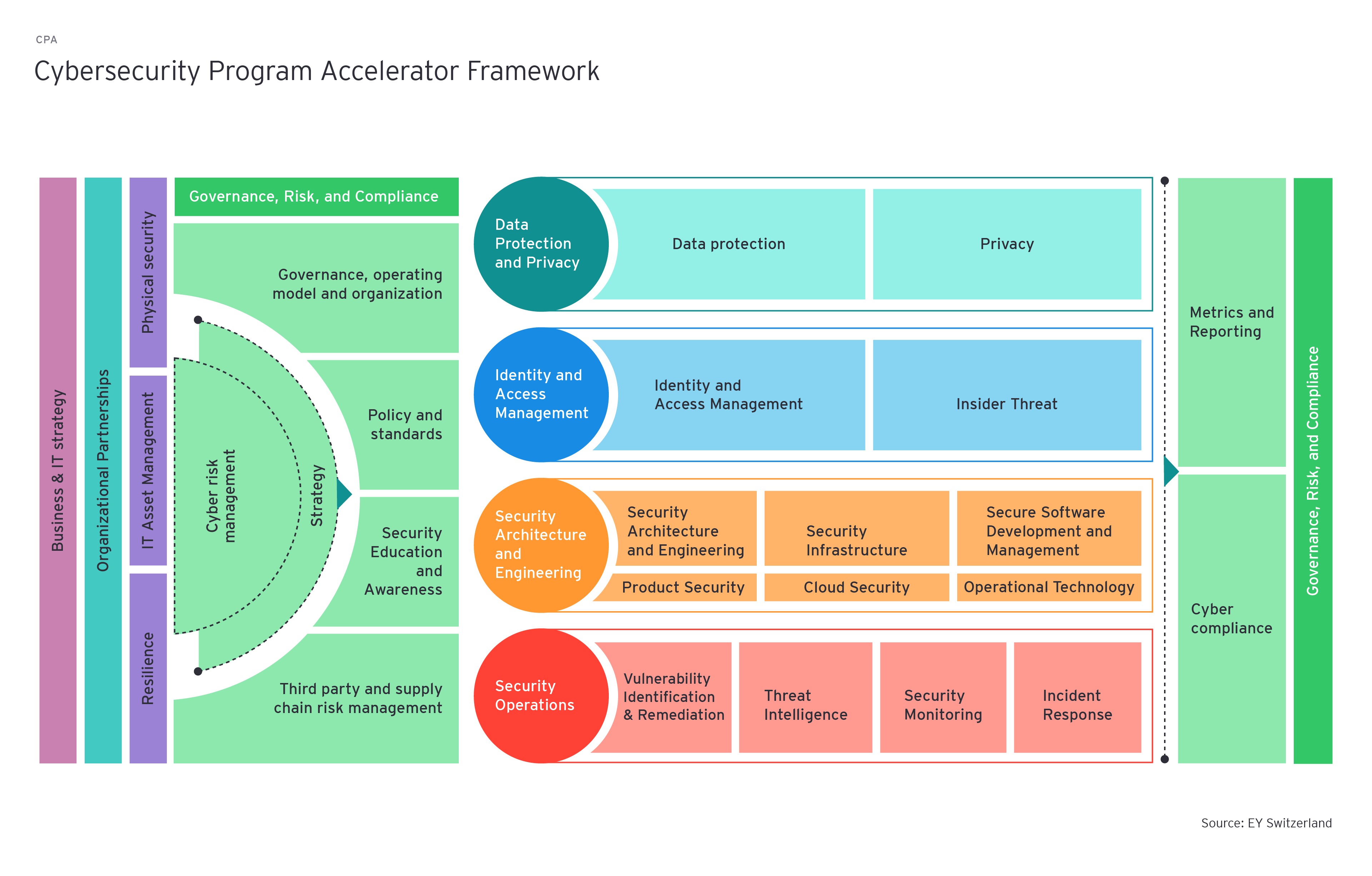
Typically, a comprehensive assessment firstly aims to understand the business context, then the risk scenarios faced by the business are determined. Next, the desired maturity profile and relevant roadmaps should be considered. One outcome of such an assessment is an action-oriented plan containing prioritized initiatives to better equip the organization to evaluate and justify the value provided by cybersecurity. Naturally, it makes sense to enrich the assessment with additional enablers to inform the cybersecurity strategy and roadmap planning, e.g., through a dedicated cybersecurity value optimization, a review of the operating model and governance structure or through a cybersecurity transformation or co-sourcing engagement.
Unclear financial impact
75%of respondents say they cannot quantify, in financial terms, the effectiveness of their cybersecurity spending in addressing the risks faced by the business
Our latest GISS study reveals that a large portion of respondents in Switzerland cannot quantify, in financial terms, the effectiveness of their cybersecurity spending in addressing the risks faced by the business. A thorough analysis is the basis for prioritizing investments and setting the scene for sustainable growth. An independent assessment often reveals more about the current state of security in an organization than internal reviews.
A comprehensive assessment, typically supported by state-of-the-art tools, enables you to rapidly assess your current state and to develop agile strategies and roadmaps to transform your organization. The value added is not only the identification of key business risks related to the maturity of specific cybersecurity domains areas, but also the alignment of the cybersecurity strategy with a focus on the organization's strategic priorities and business objectives. It enables a facilitation of a dialogue between the cybersecurity team and business leaders to articulate the benefits of cybersecurity program investments and helps to understand areas of improvement requiring additional investment. This industry-proven method helps in developing pragmatic recommendations to further improve cybersecurity programs, especially with the correct alignment of risk and cost with business needs.
Summary
No matter the organization, cybersecurity maturity level or threat landscape, it has never been more important to effectively protect your organization from cyber threats. At the same time, it’s important to embrace new technology and continually innovate to remain competitive and relevant. To address ever-changing economic, threat, regulatory and technological challenges, CISOs and security organizations must regularly and independently assess the controls and risks related to key assets of the corporation while staying within budget restrictions.


