EY refers to the global organisation, and may refer to one or more, of the member firms of Ernst & Young Global Limited, each of which is a separate legal entity. Ernst & Young Global Limited, a UK company limited by guarantee, does not provide services to clients.

New global research shows how Oceania’s financial services sector can allocate cyber budgets to the right technologies and initiatives.
In brief:
- Institutions need to revisit where they are targeting their cyber investment to improve their ability to detect and respond quickly to attacks.
- The pervasiveness of cloud, and increasingly digital supply chains, are creating an ever-expanding attack surface where 100% coverage is impossible.
- CISOs need to focus on defending critical assets, taking a holistic, balanced approach to tools and looking for opportunities to support business objectives.
New global research of cybersecurity leaders has identified high-performing cybersecurity organisations that we call “Secure Creators”. Compared to their lower-performing counterparts, “Secure Creators” have fewer cyber incidents (27 vs. 70 in 2022) and are quicker at detecting and responding to incidents (5 months vs. 11 months).
Financial institutions typically exhibit similar characteristics in their approach to cybersecurity as “Secure Creators”, including considering themselves early adopters of technology and being compliance-driven. Financial services CISOs also report their workforces are more likely to adhere to cybersecurity best practices than those in other sectors.
Financial institutions have a higher annual spend on cybersecurity than similar-sized organisations in other sectors. Of the global EY survey participants in financial services, 60% said their total annual spend on cybersecurity was USD50 million or above, compared with an average of 42% across other sectors. Driving this investment, financial institutions were more likely than other sectors to have faced 10 or more cybersecurity incidents in the last 12 months. In 2023, 56% expect cyber breaches to cost their institutions upwards of USD3 million, compared with an average 40% across other sectors.
As Boards consider the ever-more challenging cyber landscape, they are generally approving the budgets being requested by cyber leaders. EY survey found that “budget”, once a top internal challenge, was only ranked sixth out of eight in a list of obstacles in this year’s survey. Institutions are increasingly recognising cybersecurity as fundamental to business resilience, reputation and compliance and equipping cyber teams with ample support.
However, our conversations with financial services boards are now raising a different question. Rather than questioning where large cyber budgets are necessary, boards are seeking reassurance that this investment is being focused in the best way. Getting the linkages between cyber spend and cyber risk is often unclear and hard to measure. To find that line of sight, CISOs will need to look beyond technology considerations and get back to practical business issues.
Assess truly critical data and processes
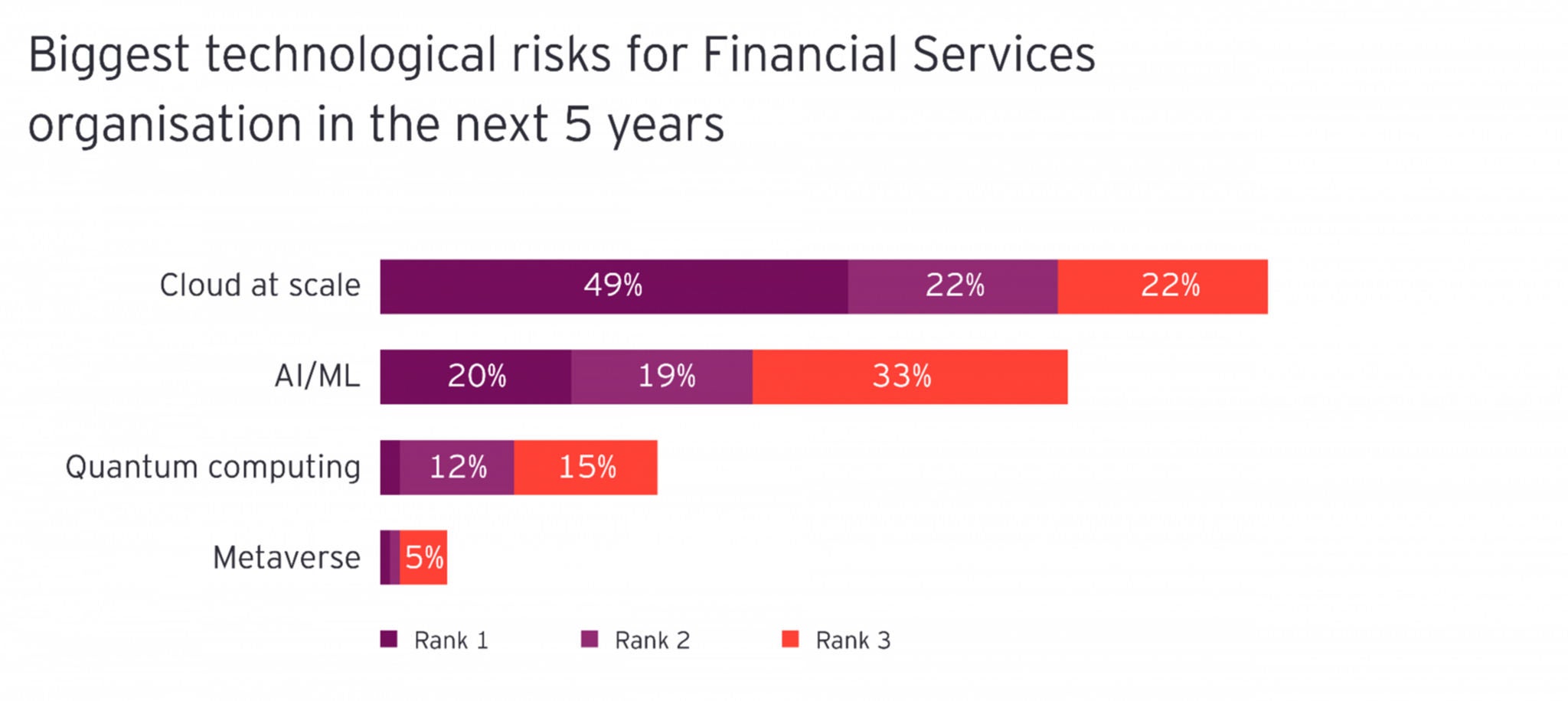
“Too many attack surfaces” was the most cited internal challenge to cybersecurity approaches. In financial services, CISOs are concerned that cloud at scale and deeper supply chains are increasing attack surfaces across cloud and third parties. More than nine in ten (93%) of the financial services survey respondents rank cloud and supply chain as their biggest cyber risks in the next five years.
In this environment, cyber defence strategies seek to protect critical assets from potential ingress. This starts with identifying those assets, which itself takes work. CISOs need to have this discussion with the enterprise, establishing what data must be protected, what functions are critical to sustaining operations and how cyber threats can impact those critical functions. It’s also important to understand what data can be deleted to reduce the data exposure landscape.
High-profile cyber breaches have helped to put personal data losses firmly on the board’s radar. Yet, as recent incidents have shown, cyber threats can also cause material operational resilience issues in the financial system. The economic (and reputational) impact of a widescale failure in digital financial infrastructure would be disastrous.
Shift the security focus onto solving business problems
Our survey found 68% of financial services Secure Creators were focusing on creating value – rather than simply protecting it. Institutions have plenty of non-cyber budgets targeting productivity or user experience improvements. CISOs who support the secure design of technology architectures to improve workforce productivity to ensure a frictionless yet secure experience for customers could command a slice of these broader business budgets.
Pick less, simplify and deploy completely
Secure Creators in financial services are more likely to describe their organisations as “early adopters of emerging technology” than the global average (82% vs. 70%). However, while the sector is certainly quick to adopt new tools, coverage tends to be limited to specific use cases. For example, some institutions have tested passwordless authentication at the proof of value stage, but widespread adoption has slow due to traditionally fragmented approach for authentication in organisations and little investment in change management for user’s reliance on password.
The reason a successful pilot implementation does not become business as usual is often because, while cyber problems cut across multiple different areas of an institution, tools are very targeted solutions that are slotted into current processes. Usually, people and process changes need to be made to ensure a tool’s features are used everywhere it can be of use across the organisation.
There is no point putting locks on windows if the front door is open. Rather than implementing point controls, CISOs should focus on taking a balanced approach to adopting new technologies to meet business requirements and respond to the changing threat landscape. For example:
- Look across the entire identity and access management architecture to design solutions and implement policies, controls for authentication and authorisation with a considered approach to business process efficiency and experience that support frictionless authentication and authorisation.
- Don’t just buy another product labelled Zero Trust. Take a step back to look at the attack surface holistically and orchestrate controls at different layers, moving from outside to inside the network.
- Consider what changes are required to standards, controls, guideline to manage the expansion of attack surface introduced through increasing adoption on AI technologies by the Business.
A critical question to ask is: Will the new tool replace or enhance existing capabilities?
A holistic approach, including investing in people (training and reskilling) and process changes, will both increase the return on the cyber investment and help to clean up the complex technological “spaghetti” that currently constitutes the cyber security operations environment.
Summary
Financial services boards and executives are seeking clarity on their cyber investments' effectiveness, relying on CISOs for optimal defence strategies. In an environment with expanding attack surfaces, the focus is on safeguarding critical assets and sustaining operational resilience. CISOs must articulate cyber spend in terms of solving business problems and consider existing investments. Simplification and consolidation of cybersecurity tools, a reduced data footprint and a holistic approach, rather than point controls, are recommended to maximise ROI and streamline the complex cyber environment in financial institutions.

