EY refers to the global organization, and may refer to one or more, of the member firms of Ernst & Young Limited, each of which is a separate legal entity. Ernst & Young Limited is a Swiss company with registered seats in Switzerland providing services to clients in Switzerland.

Defining an appropriate cyber risk appetite is key to the success of financial services organizations.
In brief
- Cyber risk appetite should be articulated around your specific business needs.
- A risk-based approach and implementation of sound practices will strengthen your cybersecurity posture
- EY proposes four phases to define your risk appetite and tolerance
How much cyber risk is your organization willing to take? If you ask yourself this question, you might first come up with the answer: none. Are you absolutely sure? Because in today’s highly connected world, a zero-risk appetite would make it almost impossible to operate. In our digital era, no matter what you do, there is always an inherent cyber risk.
Institutions from the financial services sector work in a digital economy, inter-connected to each other in order to provide secure access to their services to clients across the world. Consequently, business leaders face the challenge of defining an appropriate cyber risk appetite. Related to this, they also have to consider their cyber risk tolerance, aligned with the business strategy and in compliance with laws and regulations. When defined appropriately, an organization’s cyber risk appetite establishes internal boundaries for a thoughtful decision-making process, balances risk taking and enables new business opportunities.
Before diving into the importance of defining your risk appetite, let’s outline some of the key definitions:
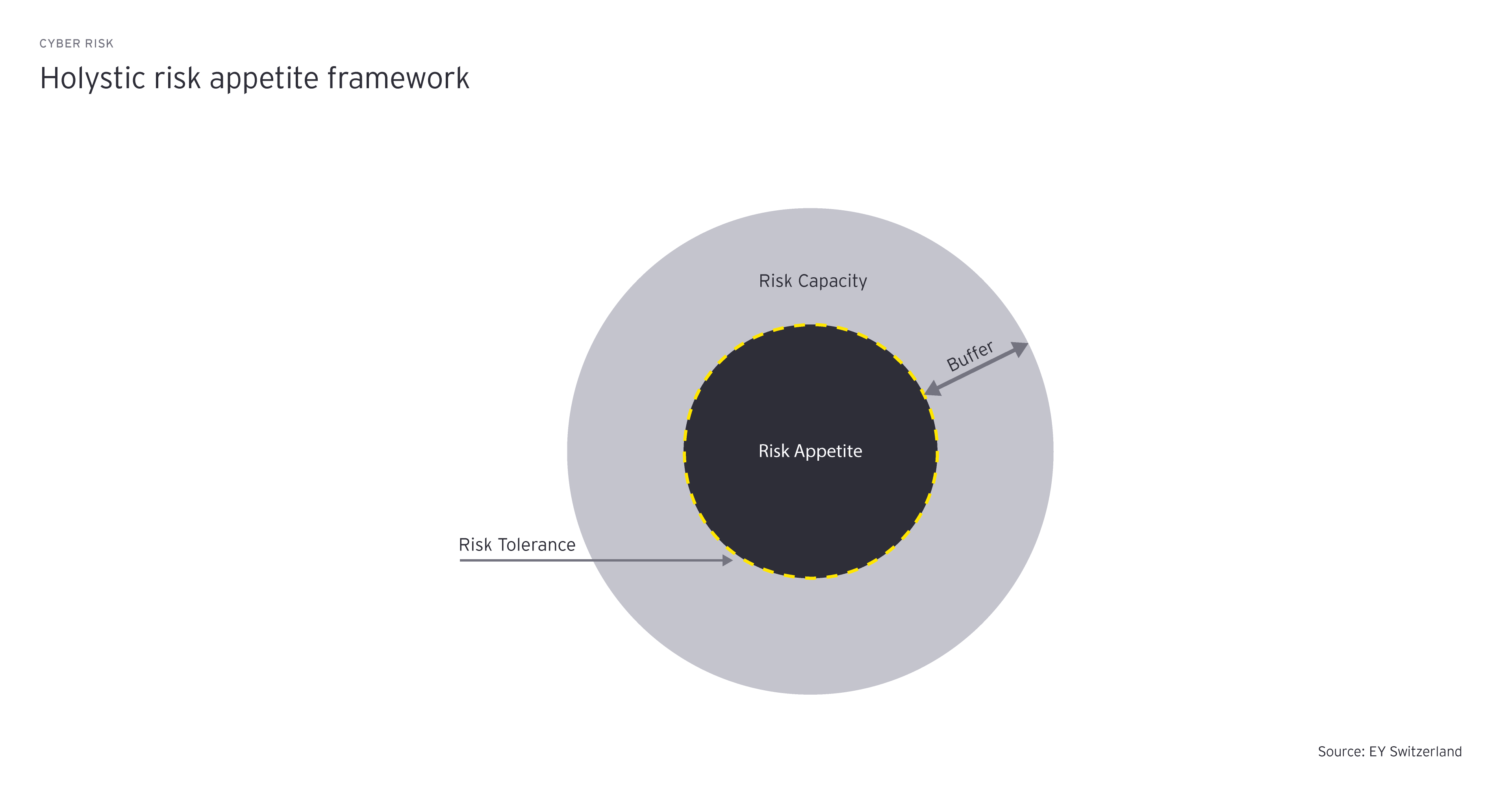
The above illustration depicts the holistic risk appetite framework. Developing a sound risk management strategy will enable a company to navigate its risk tolerance within its risk capacity boundaries. The buffer, represented by the gap between the risk capacity and the risk appetite, provides flexibility to the company, and should take into consideration the possibility of extreme outcomes as well as errors in assumptions, analysis and modeling.
Defining a well deliberated cyber risk appetite and tolerance, in line with the business activities, is key to the success of a firm. It enables business leaders to better understand what markets they should be in and what kind of business they wish to avoid. The process should consider business opportunities, risk management costs and cybersecurity implications. The organization’s business strategy should be aligned with both the risk appetite and risk capacity, which set the boundaries. An organization must be able to bring together a transparent overview of their risk exposure – and their related costs. Aside from a cost perspective, a risk tolerance framework allows the business to follow a risk-based approach to allocate its resources and determine the areas to focus on. Business leaders gain an understanding of the firm-wide alignment of risk and business opportunities, which leads to an optimized decision-making process.
To define both the cyber risk appetite and tolerance, EY has developed a four-phase approach.
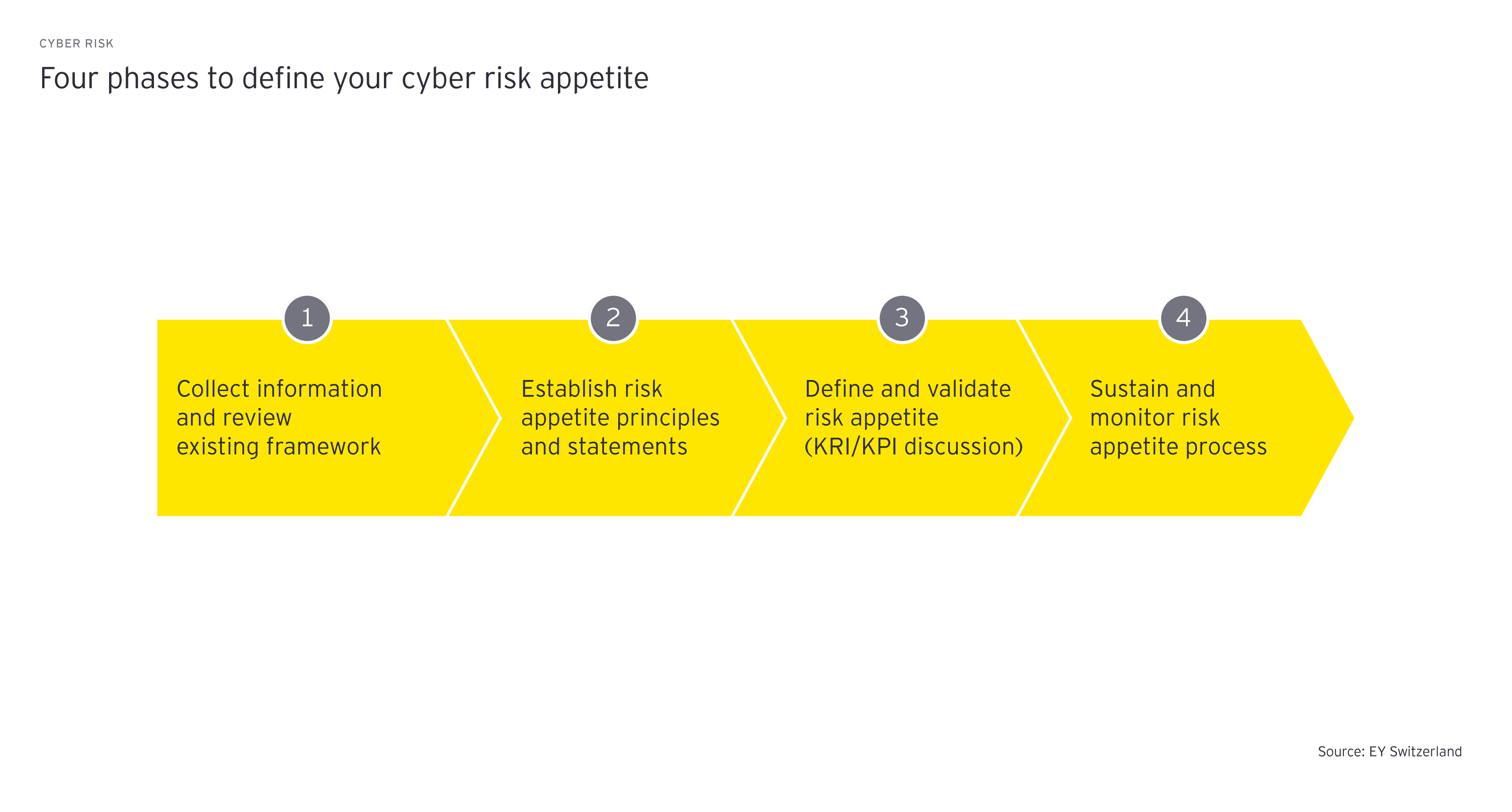
1. Collect information and review the existing risk framework
We start by collecting existing information related to the established organization frameworks. This crucial step aims to find common ground on often confusing risk taxonomy and associated risk definitions. At this stage, it’s important to work closely with enterprise risk stakeholders such as the CISO, CRO, CIO and the business.
2. Establish risk appetite principles and statements
In a second step, business leaders need to develop risk appetite principles. Workshops with key stakeholders can be helpful in efficiently defining both cyber risk appetite and tolerance. Actively involving the relevant bodies will also increase buy-in, broaden the perspectives on risk and lead to a more a comprehensive risk posture.
3. Define and validate risk appetite
A consensus on both the cyber risk appetite and tolerance statements needs to be reached with key representatives of the organization. In addition, risk metrics such as key risk indicators (KRI) and key performance indicators (KPI) need to be defined to allow continuous monitoring of related risks and enable a better understanding of cyber risk trends. This phase considers the measurement of risks related to emerging technologies and potential changes to the threat landscape in which the company operates.
4. Sustain and monitor risk appetite process
The final phase is to develop governance principles to review the cyber risk appetite and tolerance on a regular basis and ensure it remains aligned with their organization’s overall risk strategy. We advocate for the aspects of risk management that reinforce the company’s risk culture and enable it to be communicated effectively throughout the organization.
Throughout the process of defining the cyber risk appetite and tolerance, it can be helpful to have external guidance to support the establishment of KRIs aligned with underlying KPIs and related controls. Risk teams should strive to define a holistic cyber risk management framework, which is fully integrated into the existing enterprise risk management framework and supports cyber risk reporting. Investing in understanding your cyber risk appetite and the appropriate balance between the level of cybersecurity controls, cost of controls and accepted cyber risks will support you in your strategic goals and enable the business beyond cyber topics.
Summary
By defining their cyber risk tolerance, organizations set the threshold above which it is too risky for them to operate. Business leaders wishing to pursue a risk-based approach need to balance the benefits and constraints of security measures. This enables the company to maintain an acceptable level of risk, while pursuing its business strategy.



