EY refers to the global organization, and may refer to one or more, of the member firms of Ernst & Young Limited, each of which is a separate legal entity. Ernst & Young Limited is a Swiss company with registered seats in Switzerland providing services to clients in Switzerland.

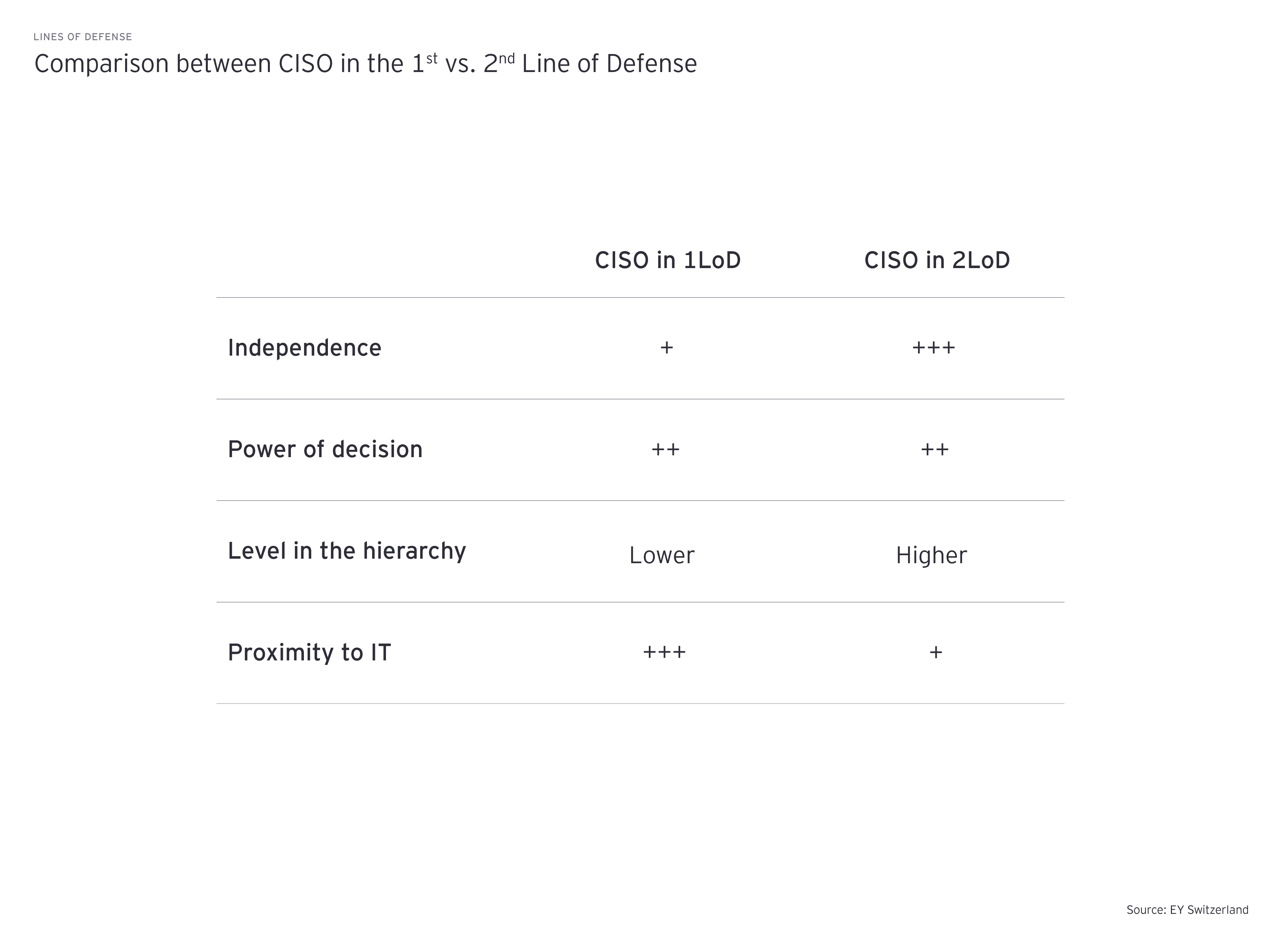
In choosing where to position the CISO, business leaders need to weigh up independence, power of decision, hierarchy and proximity to IT.
In brief
- Cybersecurity is a business-critical function for today’s financial institutions.
- Organizations have to balance various trade-offs when deciding where to integrate the CISO within the traditional three lines of defense model.
- Whatever they decide, the approach should also meet regulators’ expectations regarding segregation of duties.
Cyber threats are growing at an exponential rate around the world. The current landscape is driven by disruptive technology, like IoT, AI, 5G, the metaverse and quantum computing. Against this background, financial institutions face a growing range of cyberthreats, from hacktivism to ransomware. While some still see cybersecurity as nothing more than an operational risk for any firm, we believe it’s a critical function – and should not be neglected simply to ease digital transformation or reduce time to market.
Leading cybersecurity practices have gravitated toward a three lines of defense (3LoD) risk management model that emphasizes the separation of key roles to prevent potential conflicts of interest. In this article, we explore the three lines of defense and how they work together to mitigate an organization’s exposure to cybersecurity threats.
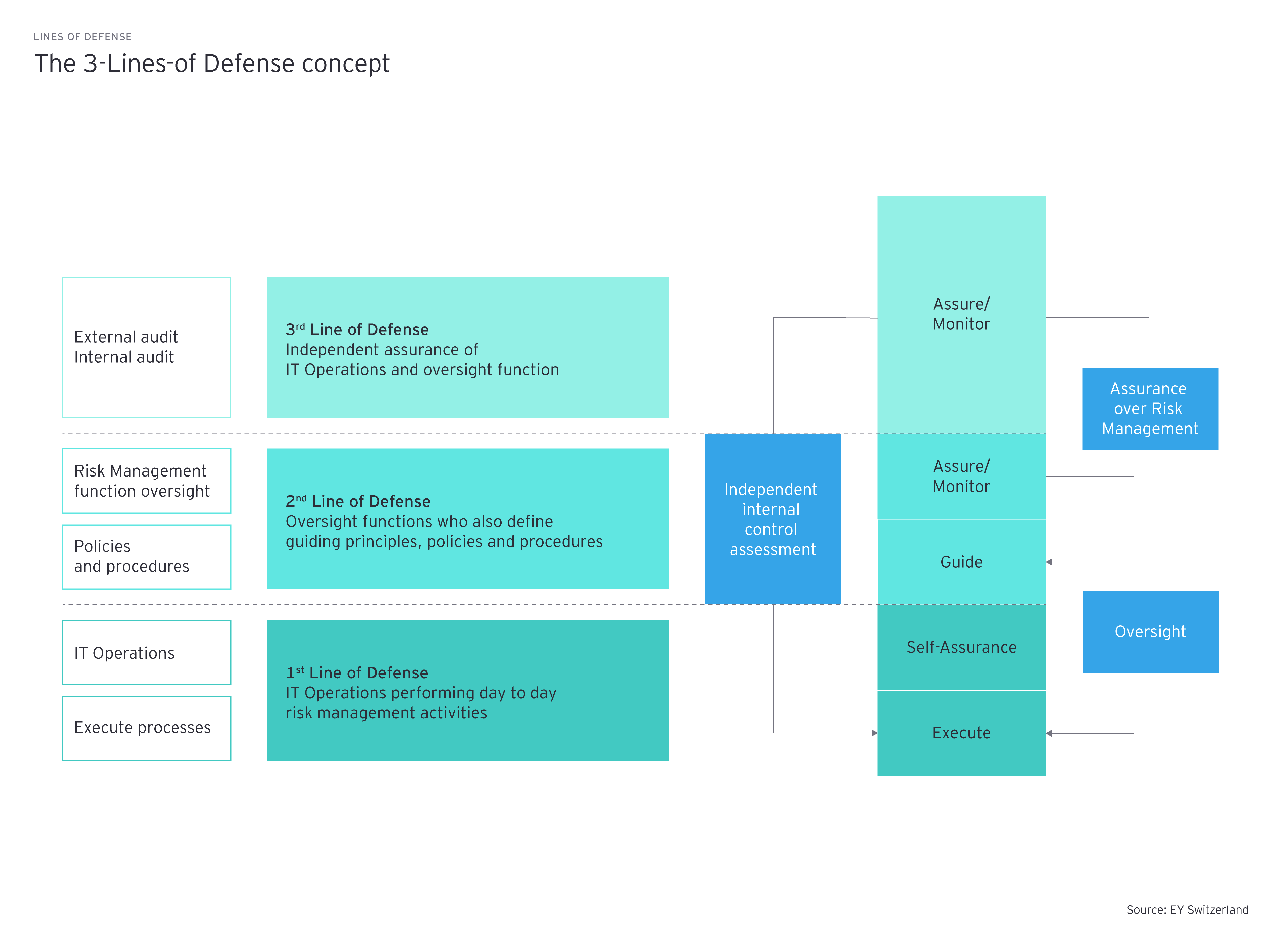
Before debating the strengths and weaknesses of either approach, let’s first establish the fundamentals. As the chart above shows, the three lines of defense are clearly allocable to different functions: IT and Cybersecurity Operations (1st LoD), Risk & Compliance including cyber risks (2nd LoD) and internal audit (3rd LoD). The 3LoD model is based on the principle of separation of duties (SoD) between each LoD, to prevent fraud and errors in the tasks.
Chapter 1
What does the 3LoD model mean for the CISO?
While each LoD contributes to the overall security posture of the organization, there are clear differences between their responsibilities.
The 2nd LoD, at the center of our risk management model, plays a pivotal role as it provides guidance on risk management while also controlling whether the guidance is effective. In a nutshell, the 2nd LoD defines the boundaries between which the 1LoD can manage its risks. Additionally, the 2nd LoD controls the effectiveness of the controls implemented by the 1st LoD to ensure that the risks are managed within those agreed boundaries. Also, the 2nd LoD is in charge of reporting the risks to management and the BoD. As a risk-taker, the responsibility of the 1st LoD is to strike a balance between enabling the business by providing the services needed and putting in place the controls necessary to safeguard the assets of the organization. The complexity of that task comes from the uniqueness of each organization, their respective risk appetite, and risk tolerance, as well as the fast-changing cyber threat landscape. Finally, the 3rd LoD, as an independent function, assesses the conduct of the other lines of defense, and reports to the senior management (SM) of the organization.
If the 1st LoD takes risks and the 2nd LoD manages and controls those risks, where does that leave the Chief Information Security Officer (CISO) or the CISO Office? Banks and insurers show differences in where they place it. Some prefer to run it as part of Risk & Compliance, while others place it closer within the IT Security function. Wherever it goes, what are the expectations of the CISO?
The CISO is essentially responsible for developing and implementing an information security (IS) program across the organization, with the aim of protecting its assets. In other words, the CISO will support the organization in increasing the information security and cyber awareness of its people, bolstering its processes, and strengthening its technology. In well-established and mature financial institutions, the IS program is structured according to industry-leading frameworks (e.g., NIST CSF, ISO 27001) to ensure a holistic and exhaustive approach.
Chapter 2
What’s the trade-off between the 1st and 2nd LoD?
There are certain dependencies between the lines of defense – and four dimensions to consider.
Each organization will have to explore individually how to best balance the advantages and drawbacks for their own needs. In this chapter, we explore the pros and cons of positioning the CISO in either the 1st LoD (scenario 1) or the 2nd LoD (scenario 2). More specifically, we will contrast four dimensions of the trade-offs:
Chapter 3
Should you position your CISO in the 1st LoD or 2nd LoD?
The short answer is: it depends. Besides your organization and overall situation, it’s worth taking into account regulators’ expectations.
Financial regulators such as FINMA or the SEC have defined principles that must be applied in order to conduct business. The interpretation of these principles is up to each organization as long as the actual implementation satisfies the regulators' expectations. For example, the Swiss financial regulator mandates segregation of duties between the parties involved in risk management (FINMA Operational Risk 08/21). While some banks address this by positioning the CISO in a different segment of the organization (2nd LoD), others implement restrictive measures that enable the segregation of duties within the same part of the organization. Thus, it is not surprising that the regulator would have greater concerns when the application of such a principle is not obvious. Likewise, if the organization faced prior cases of conflicts of interest and doubt had emerged as to the effectiveness of segregation, it may be worth considering a different setup.
To bridge this chasm, some organizations have taken an alternative approach to the traditional 3LoD risk management model: the 1.5 LoD (sometimes also referred to as 1.b LoD). This sees the 1st LoD requalified as IT Ops. Hybrid approaches like this can be observed mainly in large and complex financial institutions and consist of positioning the CISO on its own, between the IT function and the overall risk function. While this alternative model directly addresses the challenges of conflict of interests and independence of the team, it does not yet put the CISO on an equal power footing with IT Ops.
Summary
The positioning and power of the CISO in an organization will influence the risk of conflict of interest. While leaders face trade-offs in reshaping their organizational structure, consideration should be given to the four dimensions explored in this article. Additionally, insights into the industry trends, capabilities to successfully drive transformations, and close collaborations with market regulators are essential for organizations willing to shape their future cyber operating model.
Acknowledgement
We thank Anthony Kieffer for his valuable contribution to this article.
Related articles
If cyber risk is an unavoidable truth, what’s your true cyber risk appetite?
Defining an appropriate cyber risk appetite is key to the success of financial services organizations.




