EY refers to the global organization, and may refer to one or more, of the member firms of Ernst & Young Global Limited, each of which is a separate legal entity. Ernst & Young Global Limited, a UK company limited by guarantee, does not provide services to clients.

Discover the key updates the second iteration of the Network and Information Systems Directive brings and how your organization can prepare.
In brief
- NIS2 aims to get the EU up to speed and establish a higher level of cybersecurity and resilience within organizations of the European Union.
- The new Directive brings into scope more sectors and focuses on providing guidelines to ensure uniform transposition in local law across EU member states.
- Organizations should start preparing by defining their compliance roadmap and optimizing their cybersecurity awareness.
In July 2016, the Directive on the security of Network and Information Systems (NIS) was established. This Directive aimed to increase cyber resilience across the European Union through regulatory measures. It focused on strengthening cybersecurity capabilities at a national level, enhancing collaboration between Member States and incorporating cybersecurity into the DNA of organizations. The scope of organizations that had to comply with the NIS Directive consisted of two groups: the operators of essential services and relevant digital service providers.
Currently, the NIS Directive has been in effect for several years and triggered a change in mindset within the institutional and regulatory approach to cyber security. Nevertheless, it faced certain challenges where the legislation could not provide a fitting answer, resulting in a fragmented approach at the Member State level. In the last few years, the fast expansion of the digital landscape, caused by a wide array of circumstances such as the rapid sequence of innovations, the global pandemic, the cyber warfare component to the Russian invasion, etc., ensured an equal growth of the threat landscape leading to an increased number of cyber-attacks targeting organizations and Member States.
NIS2 in sight
In January 2023, the European Union adopted a new version of the Network and Information Security Directive. This “NIS2” aims to get the EU up to speed and establish a higher level of cybersecurity and resilience within organizations of the European Union.
EU member states will have to transpose NIS2 into their national legislation by October 17, 2024. Organizations should already start preparing their journey toward compliance.
In this article we explore the following key topics:
Extension of the scope
NIS2 defines two categories for entities in scope: important and essential. Entities in both categories will have to meet the same requirements. However, the distinction will be in the supervisory measures and penalties. Essential entities will be required to meet supervisory requirements as of the introduction of NIS2, while the important entities will be subject to ex-post supervision, meaning that in case authorities receive evidence of non-compliance, action is taken.
The NIS2 has simplified the scoping exercise the competent authorities have to make. A list of sectors was defined and a base rule of any large (headcount over 250 or more than 50 million revenue) or medium (headcount over 50 or more than 10 million revenue) enterprise from those sectors will be directly included in the scope. However, small or micro-organizations are not necessarily excluded; Member States can extend these requirements if an enterprise fulfills specific criteria that indicate a key role for society, the economy or for particular sectors or types of service.
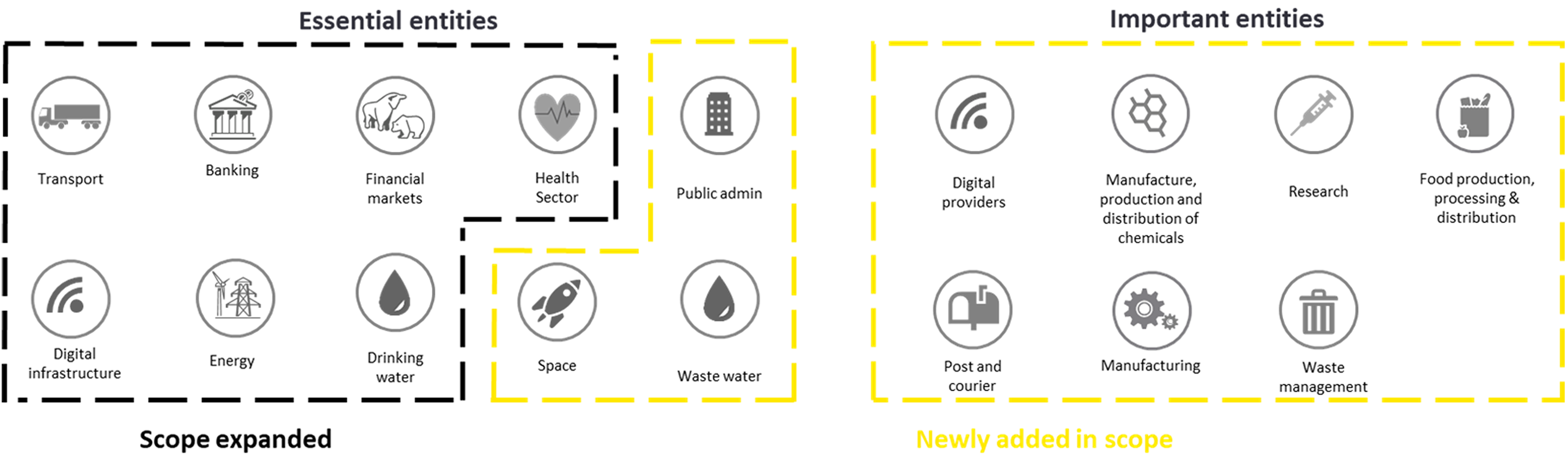
Essential and important entities registration
By April 17, 2025, the Member States must identify the essential and important entities in scope for the NIS2 Directive. Member States can enable entities to register themselves. Therefore, entities will have to determine if their services fall within the scope of NIS2, identify the list of Member States where they provide “in-scope” services and register before the deadline in each Member State. The registration will require entities to provide at least the following:
- Their name, address and registration number
- The sector or sub-sector in NIS2 scope under which they fall
- Their updated contact details
- Member states in which they operate
- The list of their assigned IP addresses
The final registration process and list of information required will be defined as part of the transposition of the Directive into law.
Improved cooperation (CSIRT platform)
Another important element of the new Directive is the intention to improve the cooperation of the EU Member States regarding cyber incidents and threats. The European Union Agency for Cybersecurity (ENISA) will be mandated to establish a European Vulnerability disclosure database to facilitate knowledge sharing between the Member States.
Incident reporting
As already established for NIS1, every Member State will have a central point of contact for compliance with the Directive and a coordinating CSIRT (Computer Security Incident Response Teams) for incident reporting or a competent authority. In Belgium, for example, this will be the role of the CCB (Centre for Cyber Security Belgium).
NIS2 has designed a new timeline for reporting incidents. Every incident with significant impact should be notified by the essential and important entities without undue delay. Within 24 hours, an early warning should be communicated, as well as some first presumptions regarding the kind of incident to the competent authority or CSIRT. After 72 hours, a full notification report must be communicated, containing the assessment of the incident, severity and impact and indicators of compromise. After 1 month, a final report must be communicated.
In that regard, the Directive encourages Member States to simplify the incident reporting process by implementing a single entry point for incidents to reduce the administrative burden, including for cross-Member State incidents.
The CSIRT, or where applicable the competent authority, has to report to ENISA on the incidents every three months, using anonymized information. With all this information, ENISA will then in turn report every six months on the EU incidents. This reporting will help organizations and the Member States to learn from other incidents and is a crucial change in the new NIS2 Directive.
Focus on key supply chains
Recent incidents all over the world have proven the importance of continuity within critical supply chains, which is why NIS2 has introduced it as one of the key focus points. Individual enterprises will be responsible for addressing cybersecurity risks in their own supply chains, as well as within supplier relationships.
This requirement might indirectly influence many suppliers who are not in the scope of the new NIS2 Directive, but they might deliver services or products to an in-scope NIS2 entity. Hence, their customer might impose a minimal cybersecurity maturity on the supplier. The supplier will not be supervised by the national authorities regarding NIS2, but by their customer. So, even if your organization is not in scope, it might still have an impact depending on the services and sector.
Accountability of the management
Another important addition to NIS1 is the accountability the new Directive assigns to the management of organizations in scope. It will be obligatory for management to take responsibility regarding their cybersecurity maturity. This will include having risk assessments conducted and approving risk treatment plans to be implemented, among other tasks. In order to perform these actions, management must follow cybersecurity training. The Directive even suggests not only to train management, but also employees, for more in-depth knowledge of cybersecurity.
Jurisdictional complexity
Under the NIS2 Directive, essential and important entities are deemed to be under the jurisdiction of the Member State where they provide their services.
If the entity provides services in more than one Member State, it should fall under the jurisdiction of each of these Member States. For entities where the service is provided or is dependent on operations outside the EU, they should ensure the continuity of their EU services in case of disruption of their non-EU operations.
Penalties
NIS1 provided penalties for non-compliance by OES and DSPs, while NIS2 introduces stricter penalties for non-compliance, including fines of up to 10% of an entity's annual turnover.
- For essential entities: administrative fines of up to €10,000,000 or at least 2% of the total annual worldwide turnover in the previous fiscal year of the company to which the essential entity belongs, whichever amount is higher.
- For important entities: administrative fines of up to €7,000,000 or at least 1.4% of the total annual worldwide turnover in the previous fiscal year of the company to which the important entity belongs, whichever amount is higher.
Anticipate and start preparing
Timely preparation is a key element in an organization’s journey towards compliance. Getting top management support, stakeholders’ buy-in and required budget and resources will take time. Anticipate the delays and commit to strict planning with hard deadlines. Moreover, implementing some of the new requirements can be considered as quick wins and set up in advance, such as the incident escalation and reporting process to the relevant authorities.
Identify your organization’s critical processes
The starting point in the compliance journey is identifying the organization’s critical services, processes, and assets that provide the essential service as defined in NIS2. A method to achieve the above is an organization-wide Business Impact Assessment to highlight the organization’s critical processes and their reliance on network and information systems. A critical element for the scoping exercise is the definition of the business impact criteria that will render a process, site or asset in scope.
Implement a risk and information security management system
Companies in scope for the NIS2 Directive will have to manage their information security risks. To achieve that requirement, a risk and information security management system must be implemented. Such an information security management system aims to identify, treat, and monitor the company’s information security risks as well as ensure responsibilities are defined and key processes are operational, such as:
- Risk management and information system security policies
- Incident handling and management
- Business continuity and crisis management (back‐ups, disaster recovery)
- Supply chain security
- Security in network and information systems acquisition, development and maintenance, including vulnerability handling and disclosure
- Policies and procedures to assess the effectiveness of cybersecurity risk management measures
- Cryptography and encryption, multi-factor authentication
- People, awareness and training
Initiate your IT supply chain security management process
Take a look at your IT suppliers, especially those that are critical for the continuity of your operations. By understanding the weaknesses of your IT supply chain and the gaps in your supplier’s security, you can start the lengthy process of remediating your contractual, operational or technical vulnerabilities.
Establish a cyber-oriented culture
One of the most mentioned elements, yet difficult to implement in many organizations, is having a cyber-oriented culture and mature information security awareness level amongst employees. Employees should be aware of their roles and responsibilities regarding the information security ecosystem. IT employees should have the required knowledge to apply the required controls. And last but not least, the management should embrace cybersecurity as a key element of the organization’s survival in this digital era.
Seek appropriate guidance and assistance in your journey
Our team of experts conquered NIS1 and is there to guide and assist you in your journey for NIS2. EY can help you assess your readiness, define your roadmap to compliance, identify your scope, set up and implement your risk and security management frameworks, secure your IT supply chain and optimize your cybersecurity awareness program.
How EY can Help
EY helps your organization achieve NIS2 compliance with tailored assessments, implementation support, incident response, and certification services.
Read moreService Leader
-
 Yannick Scheelen
Yannick ScheelenEY Belgium Consulting Cybersecurity and Privacy Director
EY Belgium newsletter
Subscribe to our monthly newsletter and stay updated on our latest insights.
Summary
The goal of the NIS2 Directive is to enhance cybersecurity and resilience in European Union organizations. This Directive expands its scope to cover more sectors and focuses on the need for consistent implementation across all EU member states. Therefore, organizations should begin preparing for compliance by creating a roadmap and increasing their cybersecurity awareness.

