EY refers to the global organization, and may refer to one or more, of the member firms of Ernst & Young Global Limited, each of which is a separate legal entity. Ernst & Young Global Limited, a UK company limited by guarantee, does not provide services to clients.
How EY can help
-
Cyber threats are evolving and escalating at an alarming rate for mining and metals, and other asset-intensive industries.
Read more
The large number of connected devices across operating environments is also contributing to the growing threat. With increasing investment in digital, reliance on automation systems, remote monitoring of infrastructure for long-term cost efficiency and near real-time decision-making across the value chain, it is the norm for M&M companies to have thousands of OT devices connected across geographical environments.
However, the increased connectivity of these devices, and by extension the increased attack surface, means that the physical security of remote M&M operations is no longer sufficient.
Additionally, equipment and infrastructure that have traditionally been disconnected (e.g., autonomous drills, trucks and trains) are now integrated to provide greater control of operations. This combination of events, coupled with system complexity and third-party risks, has led to a further expansion of the “attack paths” that may be used in cyber incidents.
For M&M organizations, there are four primary “attack paths” that can be used to compromise and impact operations across the value chain (e.g., extraction, processing or refinement, stock management and shipping). Hackers who exploit these paths frequently utilize a number of common weaknesses found within network architecture, legacy industrial technologies, basic access controls and security configurations, maintenance processes, remote staff and third-party access, and security awareness.
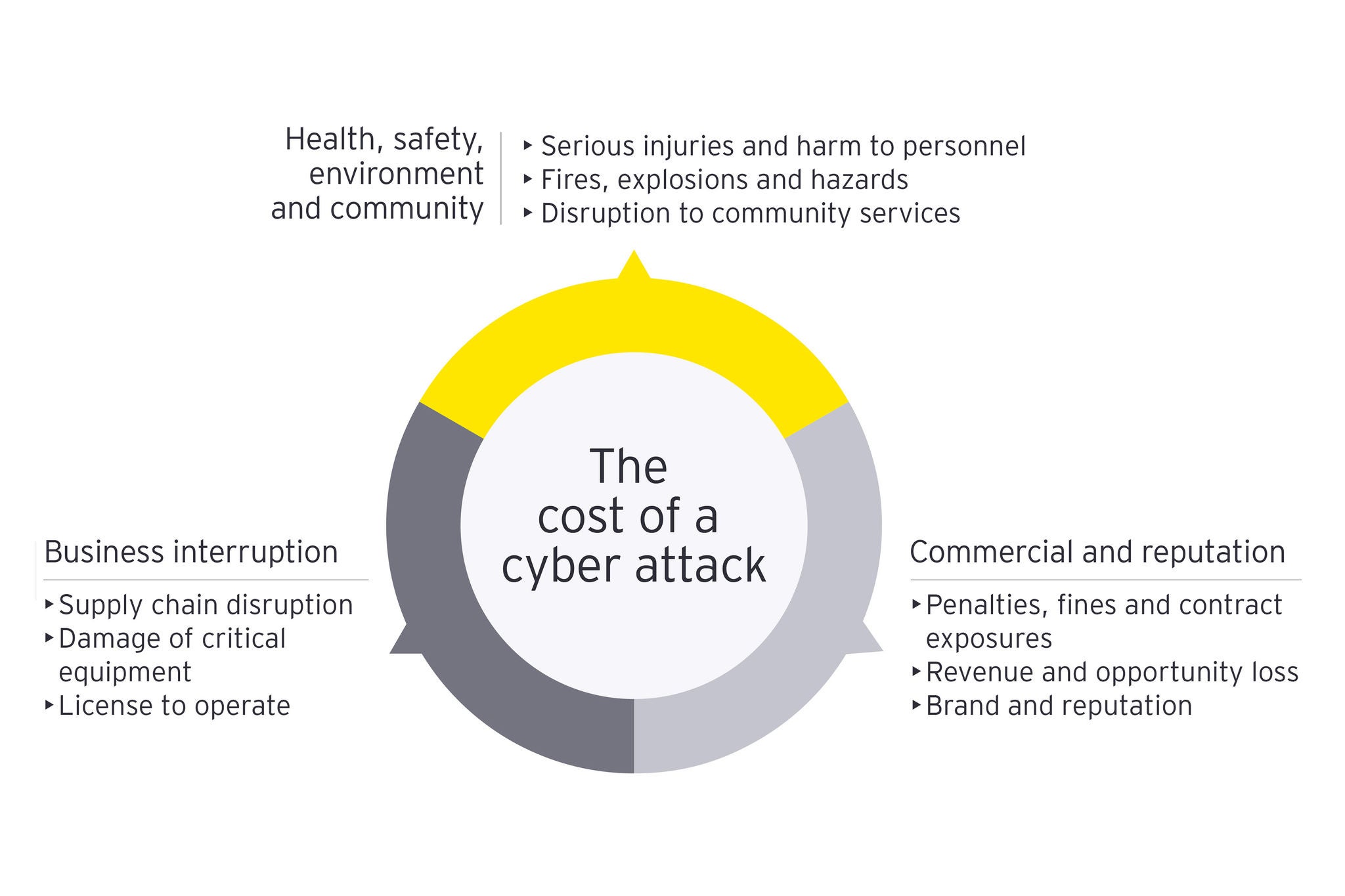
As a result, the entire supply chain is now at risk, which is not limited to the potential of causing disruptions to operations, but worse, significant health and safety consequences (resulting from shutdown or overriding of fail-safe systems, physical failure of infrastructure, equipment operating outside of expected parameters, etc.). If these risks are not being effectively identified, tracked and monitored, it is likely that the organization and its employees will be left significantly exposed. Some of our clients with strong security event monitoring solutions are seeing a rapid increase in the number of new attacks on operational systems, including viruses that are specifically designed to attack these environments.